
The Jiuzhang — Photon-based Quantum Computer
Researchers from the University of Science and Technology of China (USTC) explained in the journal Science that a Light-based quantum computer named the Jiuzhang (九章) performs a calculation in minutes. Simultaneously, a traditional supercomputer would take the world’s fastest supercomputer, Fugaku, 600 million years to complete.
What is Quantum supremacy?
Quantum supremacy is achieved when a quantum device is proven to carry out a task that a classical computer would find impossible or take too long to complete. Jiuzhang performed a quantum computation called “Gaussian boson sampling,” which is unpredictable requires handling a vast volume of data simultaneously.
China then joins Google, which claimed it reached quantum supremacy in Oct. 2019, and IBM, which has also entered the quantum computing fight. If the claims about Jiuzhang are true, it would be the fastest quantum computer in the world now.
Different from Google’s quantum machine, Jiuzhang is a light-based quantum computer. But actually, it is a setup of lasers, prisms, and mirrors. With the 76 photon detectors, it is a demonstration of using photons to form qubits (the basic unit of quantum computing — quantum bit).
This setup has claimed quantum supremacy using a quantum computation called Gaussian boson sampling (GBS). Their paper explained the usage of particles of light sent through an optical circuit, measuring the output.
What’s the impact?

Unlike what Google used to generate qubits, superconducting loops of superconductors require to cool down to a few kelvins (about –455 degrees Fahrenheit). This suggests there are multiple proven quantum-computing technologies, and definitely more to come.
Yet, that doesn’t mean that a large-scale quantum computer will be built anytime soon to solve real-life problems. Cracking the Gaussian boson sampling equation has limited application. The problem boson sampling solves: “What is the distribution of photons?
In fact, the experiment showed that Jiuzhang is better than classical computers at solving one particular task — simulating photons' unpredictable behavior. It is a setup only for solving this task.
Quantum Computing and Encryption
Over the past few years, quantum computing raises concerns about its potential impact on national security. In 2019, the U.S. National Quantum Initiative Act was signed into law. And invest more than $1.2 billion in quantum technology over the next 10 years.
But why do quantum computing is a threat to Internet Security?
In theory, utilizing quantum properties, i.e., superposition, allows quantum computers to achieve exponential speedups over their classical counterparts when applied to specific problems.
Back in 1994, the American mathematician Peter Shor discovered a quantum algorithm that defeated its classical equivalent. Shor’s algorithm factors large numbers and is the crucial element in the process of cracking trapdoor-based codes.
People worry that quantum computers will be able to crack encryption codes used to send secure messages. The codes in question encrypt data using “trapdoor” mathematical functions that work easily in one direction but not in the other.
RSA Encryption
That makes encrypting data use fewer computing resources but decrypting it hugely challenging without the help of a special key. These encryption systems have never been unbreakable. Rather, their security is based on the huge amount of time (or a huge amount of computer resources) it would take for a zero-one computer to do the job.
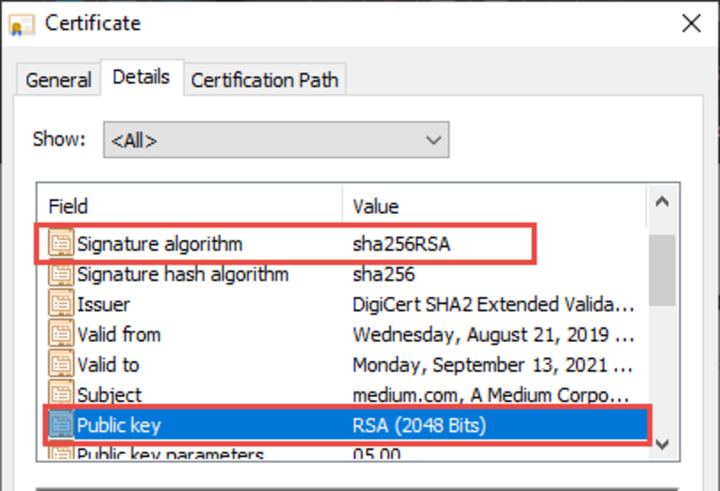
This is the basis for RSA encryption. RSA (Rivest–Shamir–Adleman) is an asymmetric cryptographic algorithm used widely in transferring data securely over the internet. Using asymmetric key encryption on the internet mainly uses two different keys between two parties, i.e., no shared secret.
It is specifically designed to decode it so long it is practically unbreakable in a digital computing environment. But for Quantum Computer, as the computing power would increase exponentially, this kind of problem would take much less time to solve, according to Shor equation.
Today’s Threat from Quantum Computing
Nowadays, the most common attack on RSA encryption ket is “The harvesting attack”. A Harvesting attack is the theft of encrypted data (ciphertext) and the RSA encryption key used to encrypt that data (private key). Multiple methods can exploit it.
Although the key was stolen is not breakable (or take too long to break) using the computer today, the people who obtained the data can store it until the theft has access to a powerful enough quantum computer someday.
Storing the data for a long time is easy and cheap, and if a quantum computer is available soon for public use, the content being stolen is at risk of being cracked and exposed.
We need quantum-safe, and crypto-agile solutions BEFORE quantum computing is practical and available to the general public. Otherwise, all existing encrypted content is at risk.
The Post-Quantum Cryptology standard

The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and classical computers and can interoperate with existing communications protocols and networks.
The National Institute for Standards and Technology (NIST) hasn’t determined its guidance yet. It is currently in the third round of a competition to decide the final Post-Quantum Cryptology standard as we advance.
According to NIST's tentative timeline, the final draft standards hopefully would be available by 2022 at the earliest. But while standards are still being developed, we can do things right now to mitigate the problem in the coming future.
The Importance of Crypto-Agility
The main goal of cryptographic agility is to enable an easy transition to alternative cryptographic schemes. There are 3 elements for Cryptographic agility, according to the Germany Journal in 2019 (DE GRUYTER):
- Cryptographic application programming interfaces
- Secure update mechanisms
- Documentation of cryptographic primitives
With Crypto-Agility in mind for deploying encryption, it could help to prepare for the transition to Post-Quantum Encryption format once it is well-defined.
Final Words
The first thing to be clear here is not to worry, at least for now, about the security threats from quantum computing to our encrypted files. But the possibilities of decrypting the data by storing it for the future.
Using what I mentioned in previous articles could be smart and is achievable now to prepare for this challenge. Mainly considerations here are Security Design, with the integration of DiD and compliances.
- Adopting a multi-layered or defense-in-depth approach to protect the system related to encryption key exchange, transfer, and storage.
- Following the FIPS 140–2 validation to implement encryption solutions is highly recommended.
- Use the Post-Quantum Cryptology Standard candidates as the encryption algorithm could mitigate the risk of Harvesting attacks.
Thank you for reading. Happy reading and Quantum Computing.
About the Creator
Z3n Ch4n
Interested in Infosec & Biohacking. Security Consultant. Love reading and running.
hackernoon.com/u/z3nch4n






Comments (1)
Quantum computing...