Decoding Blockchain Security: How Cryptographic Hashing Fortifies the Digital Realm
Uncover the power of hashing in blockchain security. Explore how cryptographic hash functions fortify data integrity in the digital realm. Discover the future of trust and transparency in our in-depth exploration.
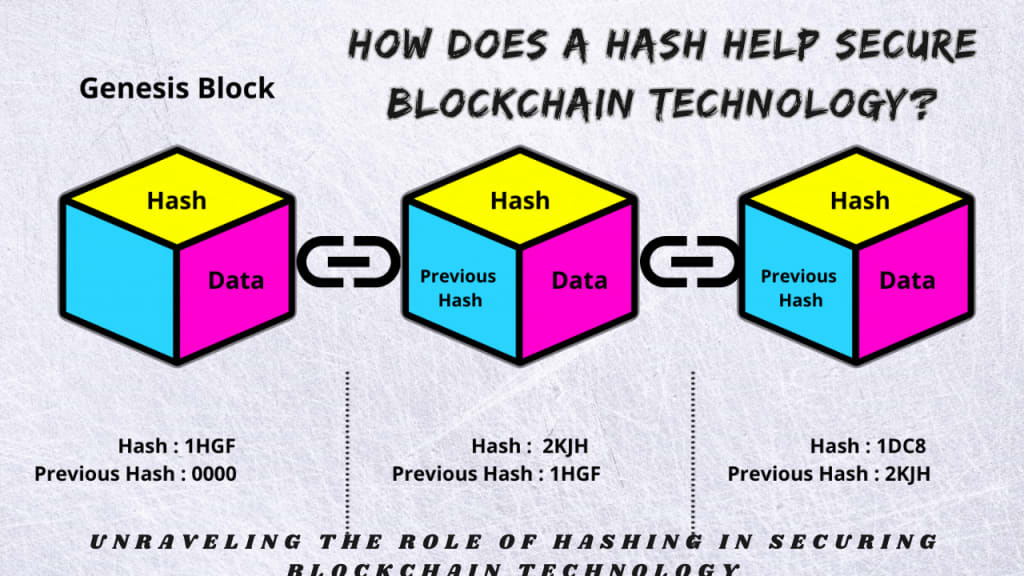
In the realm of digital trust and transparency, blockchain technology stands as a formidable citadel. A critical guardian of this fortress is the enigmatic world of "hashing." This article embarks on a profound exploration of hashing, the digital locksmith that stands as an unyielding shield against data manipulation and breaches.
Understanding Blockchain Technology:
At the heart of this journey is the understanding of blockchain technology. Picture it as an open ledger, distributed across a network of computers. Each transaction is recorded with unbreakable transparency, and there's no central authority holding sway. Decentralization is the hallmark, ensuring no single entity has the keys to this digital kingdom.
The Role of Hashing in Blockchain Security:
As we unlock the gates of blockchain security, the process of hashing takes center stage. It's the transformation of data into a fixed-size string of characters, creating a unique fingerprint, or hash. Importantly, this transformation is one-way, ensuring the original data's inaccessibility.
Cryptographic Hash Functions:
Cryptographic hash functions are the sentinels of this realm. These functions are engineered to be secure, irreversible, and immune to collisions. It's the digital equivalent of turning data into an unassailable vault, guaranteeing that data remains tamper-proof.
How Hashes Secure Data on the Blockchain:
Envision each transaction on the blockchain as a sealed envelope. Hashing, our digital guardian, affixes a unique seal—the hash value. This seal becomes an indelible mark of that transaction. Should any tampering occur, the intruder would not only have to alter the transaction but also recalculate the hashes for all subsequent entries. It's a formidable fortress, virtually impenetrable.
Protecting Against Tampering:
Blockchain's hallmark is public verification. Each participant can independently verify the data's integrity by checking the hash values. Any unauthorized modification sends shockwaves through the network, serving as a signal of potential intrusion.
Examples and Use Cases:
The applications of this technology are as diverse as the digital realm itself. Blockchain's transparency and security, enforced by hashing, are the cornerstones of various industries. From supply chain management to healthcare, voting systems, intellectual property, and beyond, our guardian ensures data remains inviolable.
Challenges and Future Developments:
While our guardian is resolute, challenges loom on the horizon. Scalability, energy consumption, and regulatory concerns cast shadows over this digital realm. Yet, the future holds promises and solutions that address these issues. Sharding, energy-efficient consensus mechanisms, and advancements in post-quantum cryptography pave the way for a more secure and efficient digital landscape.
Blockchain and Beyond A Glimpse into the Future:
In the vast universe of blockchain technology, our guardian, hashing, is not merely a sentinel; it's the cornerstone of data integrity and security. As we navigate this ever-evolving landscape, understanding the role of hashing is not just essential; it's transformative. Here's a glimpse of the future this guardian promises.
1. Enhanced Privacy:
Privacy concerns have become paramount in our digital age. Emerging solutions focus on providing users with greater control over their data while maintaining impeccable security. These solutions are game-changers, offering newfound digital sovereignty.
2. Sustainable Blockchain:
Energy-efficient consensus mechanisms, such as Proof of Stake (PoS) and Proof of Authority (PoA), are increasingly replacing energy-intensive systems like Proof of Work (PoW). This shift not only reduces environmental impact but also makes blockchain more sustainable for a wider range of applications.
3. Cross-Chain Integration:
Blockchain's interoperability is the bridge between isolated islands. With the development of cross-chain protocols, data sharing becomes seamless between different blockchains. This expands the horizons of blockchain applications and makes them more versatile.
4. Regulatory Clarity:
As regulatory frameworks continue to mature, the blockchain industry gains more certainty and legitimacy. Clearer regulations provide a framework for responsible and secure blockchain development, reassuring users and investors.
5. Post-Quantum Cryptography:
The advent of quantum computing poses a looming threat to existing cryptographic algorithms. Post-quantum cryptography research is diligently working on safeguarding blockchain against this future threat.
In the digital realm, where trust and transparency are the bedrock of innovation, blockchain technology fortified by cryptographic hashing stands as a sentinel of invulnerability. It's not merely a guardian; it's the fortress itself, defining trust and security for the digital age. As we navigate this ever-changing landscape, understanding the role of hashing isn't just an insight; it's empowerment.
At the crossroads of innovation and security, blockchain and hashing intersect, promising a future where trust, transparency, and security aren't mere ideals but the very essence of the digital realm.
Visit technest.blog for more tech articles
About the Creator
Technet.blog
Dive into our Vocal stories, where every piece is a tech revelation. We're here to keep you informed, inspired, and engaged. Feel free to comment, share, and let your tech passion shine!
📌 Discover More on Our Website: www.technest.blog






Comments
There are no comments for this story
Be the first to respond and start the conversation.