Moral Hacking as a training incorporates surveying and finding the breaks in a computerized framework that a noxious programmer can exploit. These breaks help the vindictive programmer in giving an easy manner to enter and hurt the framework or notoriety of the hacking casualty. Hence, a guaranteed moral programmer will harden the current security levels while finding any provisos that might be taken advantage of. Hacking experts should remember morals and give wanted digital protection to people, firms, or states from the danger of pernicious hacking and security breaks. In addition, moral Hacking is finished with the assent of the concerned clients to upgrade the wellbeing of their web-based presence.
CEH preparing on the web is a great method for understanding and execute the vital ideas of moral hacking and ways of getting everything done well. These preparation programs assist you with mastering many abilities and techniques to utilize them and defend delicate data on the web.
This instructive article will furnish you with an itemized prologue to moral hacking to assist you with grasping the related key ideas. Moreover, it will give a point by point separation between moral programmers and programmers with vindictive expectation.
What is a Moral Programmer?
A moral programmer is a prepared proficient employed to give first rate online protection to people, firms, and states by legitimately hacking into their frameworks and recognizing any points of weakness. A Moral Hacking course can assist you with building a profession as a Moral Programmer. Get network safety course subtleties and seek after it to figure out the rudiments.
What are The Vital Ideas of Moral Hacking?
The vital ideas of moral hacking recognizes it from different types of hacking rehearses. Prior to starting with the "kinds of programmers" and the interaction followed, getting a moral hacking outline of the key ideas is basic.
Lawfulness - Prior to starting the course of moral hacking, programmers ought to get due consent and legitimate endorsement (a Should do).
Scope - Moral hacking can be broad or shallow contingent on the client's necessity. Understanding this degree is significant prior to beginning the errand.
Report - When the method involved with hacking is finished, every one of the weaknesses or security issues ought to be appropriately answered to the concerned groups.
Information Protection - Moral programmers frequently run over information and delicate data and, consequently, may require marking an agreement before they start working.
What are the Types of Hackers?
There are three sorts of Programmers - White Cap, Dark Cap, and Dim Cap Programmers.
White Cap Programmers - These are the "Moral Programmers" who endeavor to hack into a framework for the advantage and security of the framework. This sort of hacking is legitimate and is utilized by people, of all shapes and sizes firms, and, surprisingly, the public authority to test their frameworks, track down any shortcoming and fix it. White Cap programmers work with the attitude of the noxious programmers however with honest goal. They utilize various techniques to break the security walls by means of weakness appraisals, infiltration testing, and so on. The framework proprietors frequently utilize these programmers.
Dark Cap Programmers - As the name proposes, these kinds of programmers attempt to acquire unapproved admittance to security frameworks and information frameworks with the expectation to hurt. Their goal can be taking touchy data (which they can sell illicitly), stop the tasks cycle of a firm, harm the framework forever, and so forth. This is all an unlawful and culpable offense.
Dark Cap Programmers - These sorts of programmers are some place in the White Cap and the Dark Cap programmers. That is on the grounds that these programmers exploit the shortcomings of a framework without the proprietor's consent, however it isn't finished with any pernicious expectation. These programmers do this for their tomfoolery or to figure out how to hack, yet when they are fruitful, they normally illuminate the proprietor about the flimsy part. Despite the fact that this sort of hacking is managed without noxious plan, it is for sure an offense. Subsequently, on the off chance that somebody is keen on learning moral hacking, the best game-plan is to sign up for a prologue to a moral hacking course in Hindi or English.
What are the kinds of Hacking?
There are various manners by which a framework can be hacked -
1. PC Hacking or Framework Hacking - This kind of hacking incorporates unlawfully accessing individual frameworks or PCs inside an organization. This is much of the time seen when the objective is particular, or the design is to take data from an organization of PCs. It is the occupation of moral programmers to attempt to get into the frameworks to recognize the flimsy spots.
2. Network Hacking or Remote Organization Hacking - Remote Hacking is the most common way of taking, catching, or observing the remote bundles inside a specific organization. When a programmer gains admittance to the remote organization, they can likewise get to passwords, talk meetings, client history, and so forth. Moral Programmers utilize comparable strategies to break the remote organization and find new and various ways that Dark Cap programmers can utilize.
3. Email Hacking - In the advanced universe of the corporate area, messages contain very delicate information and data that programmers might be keen on. Email hacking can incorporate hacking into the organization to receive email passwords and acquiring unapproved admittance to the email of an individual or workers of a business. This can uncover a singular's very own life or uncover touchy information from business messages. A phishing assault (boundless) can likewise prompt clients undermining their own data or information security.
4. Site Hacking or Web Application Hacking - Exploitative programmers could show interest in hacking sites or web servers as it can adversely influence a business. This can prompt the site being down for expanded periods (loss of business, openness, and acknowledgment), robbery of programming and information base, and, surprisingly, super durable harm. Notwithstanding, moral programmers endeavor to do this with consent and afterward recommend how the breaks can be fixed.
5. Secret phrase hacking can be a piece of PC or framework hacking. Programmers use the information put away on the PC and on the servers to get to the passwords to any site, PC, email, accounts, and so forth., and afterward utilize that data for noxious purposes. Moral programmers utilize comparable strategies to do so and recognize any safety efforts that can be followed to forestall this.
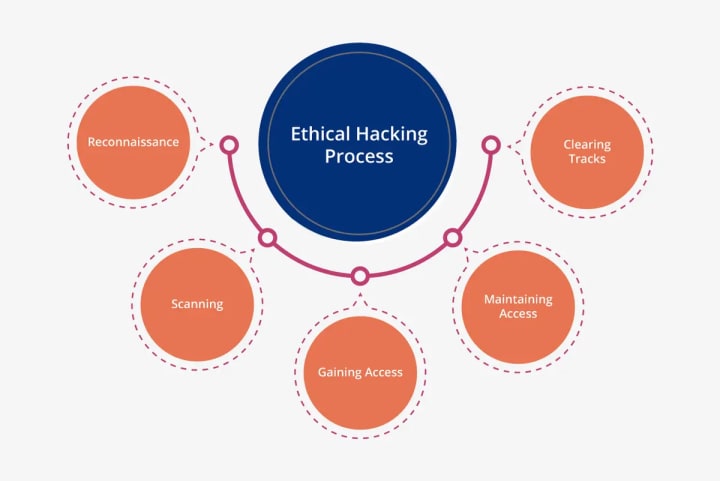
Periods of Moral Hacking
There are five periods of moral hacking to guarantee that every one of the foundations of online protection are covered while moral programmers test an association's organization. These stages help in figuring out the essentials of moral hacking.
Observation - This is the primary period of moral hacking and is many times known as the preliminary stage. In this stage, a moral programmer will assemble adequate data, make an arrangement, and plan for the assault. Inside surveillance, the main stage is Dumpster Jumping, where a moral programmer desires to track down helpful data like old passwords, data sets of representatives, clients, filed monetary data, and so forth. The following stage is footprinting, where the programmer will gather the important and required data for the hacking system, for example, security structures, IP addresses, and so on.
Examining - Checking is the method involved with getting speedy admittance to the external level of the security structure of any organization or framework. Yet again programmers search for important data in this stage. The initial step is pre-assault checking, where data from surveillance is utilized to accumulate more data. The subsequent step is sniffing or port examining, where a programmer utilizes instruments like weakness scanners, port scanners, dialers, and so on., to overview the organization. Ultimately, data extraction is where data about the ports, actual machine, and framework subtleties is accumulated to plan for the hacking assault.
Getting entrance - When all the applicable data is accumulated, the following stage for the programmer is to get close enough to the organization or the framework. When this occurs, the programmer obtains entrance and unlimited authority over the organization subtleties and individual frameworks.
Keeping up with Access - After a moral programmer accesses the framework, they will keep on keeping up with the assault to permit adequate chance to assemble the data required or complete the reason for hacking. Extra goes after are likewise sent off if the programmer needs additional time or believes that should cause more harm.
Covering Tracks - Getting away from the security staff and the security structure incorporated into the framework is just about as significant as obtaining entrance. This is finished by following advances like shutting open ports, erasing the log records, clearing all treats, and so forth. This guarantees that the hacking endeavor can't be followed to the programmer.
What Abilities and Confirmations should a Moral Programmer get?
A portion of the normal abilities that are expected to turn into a moral programmer incorporate -
Programming Information that is expected while working in the field of organization security.
Prearranging information to distinguish and manage assaults.
Network abilities, as most malevolent hacking assaults are focused on the organization. Appropriate information on PC organizing is expected to assist with tracking down the defects in the framework.
Essential information on working frameworks like Windows, macOS, Linux, and so forth.
Forward-thinking information on new hacking strategies, devices accessible, hacking designs, and so forth.
A definite prologue to moral hacking can assist you with the most common way of fostering the expected range of abilities.
Jobs and Obligations of a Moral Programmer
The jobs and obligations of a moral programmer incorporate ;
- Getting appropriate authorization from the association to association
- Understanding the extent of hacking and what the necessity is
- Have a similar outlook as a noxious programmer and find manners by which security can be penetrated
- Report the issues to the groups worried to assist with tracking down an answer
- Keep any disclosure of imperfections and any touchy data classified
- Not leave any hint of hacking to shield malignant programmers from utilizing similar breaks.
What Issues Does Hacking Recognize?
A portion of the normal issues that moral hacking tackles are - it can distinguish pilfered content on association frameworks, passwords that have been uncovered, security levels that are not sufficient, network insurance settings that don't give sufficient security, and so on.
Impediments of Moral Hacking
A portion of the normal impediments of moral hacking incorporate -
The course of moral hacking, on the off chance that not done cautiously, can harm the inside frameworks and records or even eradicate information.
Despite the fact that moral programmers are frequently made to sign agreements before they start working, the data they see during their work might be utilized for individual addition or vindictive use.
As moral programmers will approach the company's frameworks and organization, it can bring up an issue of worker security and the protection of client information.
Moral Hacking Advantages
- Moral hacking has benefits that help recognize and check any malevolent assaults to take information, cause issues for an individual or a business, bring public safety in danger, and so on.
- The absolute most significant advantages are -
- The formation of a solid organization is the most important phase in guaranteeing low responsibility. Subsequently, moral programmers likewise assist with making a protected organization from security breaks.
- As far as public safety, moral hacking assumes a critical part. Blocking data with respect to computerized psychological oppressor assaults, safeguarding information from malignant programmers, and protecting the public frameworks from security breaks are a portion of the familiar manners by which moral hacking is valuable.
- Moral hacking builds up the advanced construction of the concerned association. It recognizes and distinguishes the fundamental provisos and guarantees to go to important lengths to stay away from splits the difference in security.
- Moral hacking likewise assists organizations with laying out entrust with their clients. Unwavering quality among clients assists them with building a steadfast client base. Security of the item or administration and the client information assist organizations with prospering in their area. Information is one of the most basic resources of organizations, and it is their obligation to guarantee that it is completely safe.
- In the event that you have fostered an interest in this space, get enlisted to KnowledgueHut's CEH preparing on the web and get everything rolling with a lifelong in moral hacking.
End
You can begin your Moral Hacking vocation by taking a confirmation course and acquiring pertinent viable experience. Understanding the basics and it are fundamental to get hypothetical information. Notwithstanding, functional experience will assist you with understanding the cycle better. Network safety is a critical piece of the present security structure. With lots of delicate information put away with outsider administrations, safeguarding that information has turned into a critical undertaking.
Watch some html and css projects;





Comments
There are no comments for this story
Be the first to respond and start the conversation.