The landscape of cybersecurity is changing at pace. Many companies find it challenging to manage the increasing number of threats, and also figure out the real risks from false alarms. For battling this many organizations have decided to build their own security operation center.
The role of this is to reduce the risks of cyber threats in real time. But if you want to set up your own SOC, it can be really an expensive affair.
An alternative to this is SOC as a service, and we will read about the same in this blog.
Understanding SOC as a Service
When we talk of SOC as a service, it is nothing special, but just outsourcing all of the security operations of a company to a third party. Rather than spending a huge amount money in hiring and keeping a dedicated team in the company to look after all the security operations, all the security operations can be outsourced. These saves a lot of funds on the part of the companies, without putting additional strain on the IT department.
The third party works with the IT security staff of the company, and can manage the threat monitoring and mitigation of risk.
SOC as a service, also gives businesses the prospect to engage a group of people with deep knowledge and skill set when it comes to evolving security technology.
Why it is Preferrable to Choose SOC as a Service?
API Security
This is a major apprehension for businesses as they install more web applications reliant on on the use of APIs, particularly when making use of those provided by a third-party developer. The SOC as a service provider examines the APIs being used, reports the vulnerabilities and provides solutions for them.
Enhancement of Endpoint Security
Many businesses oversee the endpoints where these connections originate from and dismiss at. Cyber attackers know about this and it is a main target. SOC as a service teams have the expertise to strengthen these endpoints, improving overall security.
Access to AI
In addition to offsetting IT security staff filtering through false threats, SOC a service tam can access other kinds of intelligence that can be put to use for strategic initiatives such as building out AI tools. By merging data from different sources, it paints a comprehensive and realistic picture of the landscape of cyber threat.
Upholding Regular software Updates
A key rule of cyber security is to make sure that the business is doing software updates in a timely manner. Though, this can be missed, making systems susceptible. SOC as a service ensures all updates are applied on a regular basis.
Coming to a Close
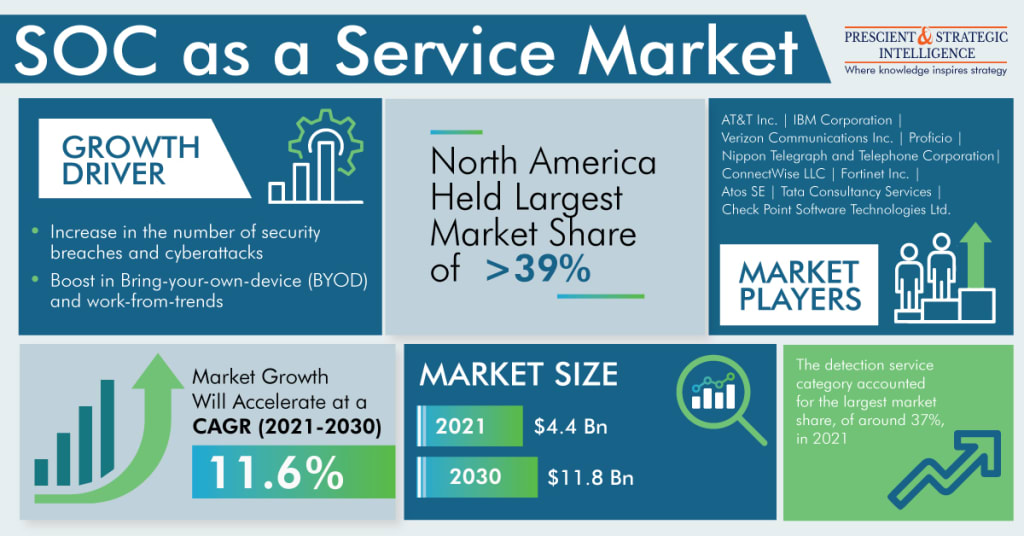
Due to the increasing number of security breaches and cyberattacks taking place all over the world, the demand for SOC as a service is on the rise, and the total demand will reach a value of 11.8 billion, by the end of this decade.
Key Players in Security Operation Center as a Service Market Are:
- AT&T Inc.
- IBM Corporation
- Verizon Communications Inc.
- Nippon Telegraph and Telephone Corporation
- Proficio
- ConnectWise LLC
- Fortinet Inc.
- Atos SE
- Tata Consultancy Services
- Check Point Software Technologies Ltd.
About P&S Intelligence
P&S Intelligence provides market research and consulting services to a vast array of industries across the world. As an enterprising research and consulting company, P&S believes in providing thorough insights on the ever-changing market scenario, to empower companies to make informed decisions and base their business strategies with astuteness. P&S keeps the interest of its clients at heart, which is why the insights we provide are both honest and accurate. Our long list of satisfied clients includes entry-level firms as well as multi-million-dollar businesses and government agencies.




Comments
There are no comments for this story
Be the first to respond and start the conversation.