SCAM ALERT: COVID-19 Test Results Email
Another scam to keep you on your toes

Using every opportunity that comes their way, scammers have, unsurprisingly, jumped on the COVID-19 bandwagon with this little gem.
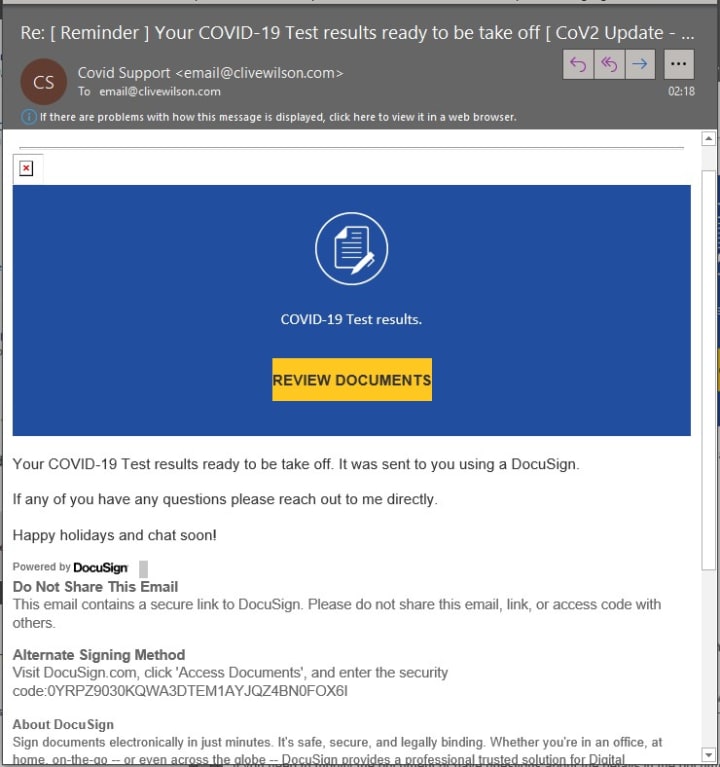
This particular scam, or versions of it, is not new, but I received it in my email inbox today and felt it was worth sharing.
COVID is the single, most current topic on anyone’s mind.
It has affected individuals, families, companies and whole countries, so it’s perfect for scammers to use it as a platform as everyone is over-sensitive to anything COVID related and are likely to believe there’s at least something genuine about the communication they’ve received.

How would you know this is a scam email?
Scammers are generally not very intelligent and pay little attention to the all-important details — but they’re often details you will easily miss.
They think they’re being smart, but the omission of a single word can be a red flag to the majority of people. Don’t be that person who ignores the flags and continues without questioning anything.

LOOK AT THE WORDING
The subject line of this email scam is:
Re: [ Reminder ] Your COVID-19 Test results ready to be take off [ CoV2 Update — 735167 ]
There are so many things wrong with this subject line.
The subject line of a new email does not begin with "Re:". That’s what is put there when you reply or forward an email.
"Reminder". I haven’t received anything prior to this.
"…ready to be take off." Does it look right to you?
‘[Cov2…]. What even is that? Nobody refers to it as ‘Cov’ and what does the ‘2’ relate to?
Read what the subject line actually says, not what you think it says. Say it out loud if necessary so that you hear it as well as see it.

WHERE HAS THE EMAIL COME FROM (who sent it)?
The email I received was sent from… my email address.
The account name was ‘Covid Support’, but it was my email address. That is classic spoofing. You should N E V E R accept (read/open/respond) to an email that is sent to you from YOUR email address if you didn’t send it.
If you are emailing yourself and you respond to the email, it’s probably a sign that you need to get out more.

WHAT IS THE TONE OF THE MESSAGE?
The email I received said:
If any of you have any questions please reach out to me directly.
Happy holidays and chat soon!
Now, an email of this nature would most likely have been sent by a Government agency managing the COVID-19 test results.
Does it feel right that I can ‘reach out’ to them directly (especially when the email came from me)?
Would they really wish me ‘Happy Holidays’ (an American term — I’m in the UK), or suggest that we can ‘chat soon’? I don’t think so, do you?

ARE THE LINKS GENUINE?
This is a tricky one, so pay attention!
The ultimate goal of scammers is to get you to click on a link or button.
Some links will take you to a form to complete (that’s phishing, and is how they will capture your personal information), whilst some will secretly download a packet of malware that will attempt to infect your PC.
DO NOT, UNDER ANY CIRCUMSTANCES CLICK ON ANY LINKS until you are 100% sure that everything about the email is genuine.
So, how do you know if a link or button is genuine?
On a desktop/laptop, simply hover your cursor over the link or button and observe the link address that pops up. On a mobile device, press down on the link until the address pops up but DO NOT tap/click it. Press, hold, see the link and release.
Here’s what the big, enticing yellow button showed on the email I received:
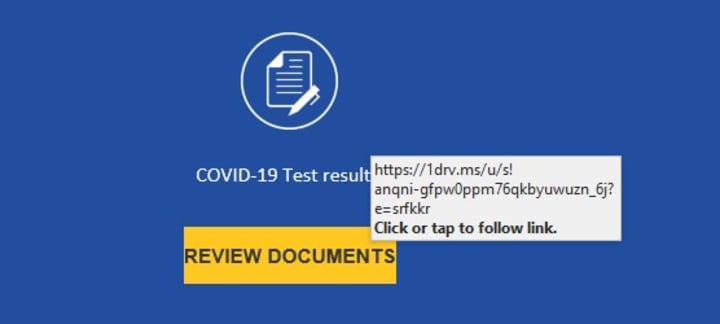
Clearly, this link doesn't look safe.
If you hover over links on a trusted email newsletter, you will often see a string of characters at the end of the domain name. Here’s one from my Goodreads newsletter:
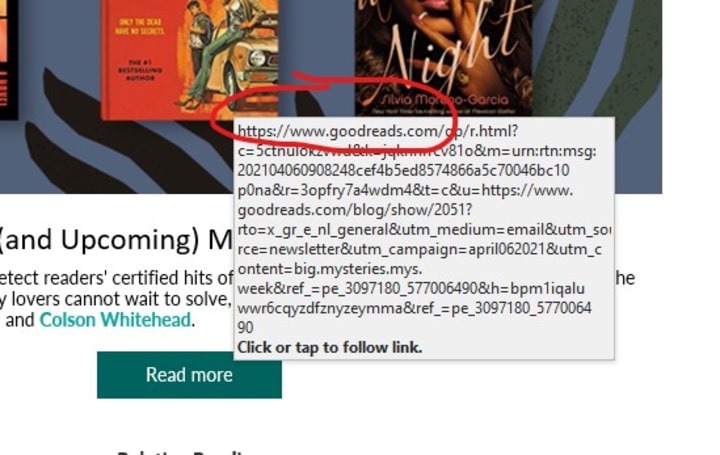
Can you see the beginning of the link is the Goodreads domain name, followed by a string of weird characters? The latter is usually a tracking code inserted by an email marketing platform to enable the sender to measure how effective the email has been. All pretty standard stuff.
Knowing and trusting the domain name is absolutely crucial. If you refer back to the image above of the link in the scam email I received, the domain name is 1drv.ms — clearly nothing whatsoever to do with any Government agency (the .ms domain name extension is from Montserrat, a tiny Caribbean island in the Lesser Antilles), nor anything I would be likely to trust.
If you don’t trust it, don’t click it.

SIX KEY POINTS TO TAKE AWAY THAT WILL KEEP YOU SAFE
- Slow down your instinct to click on every email you receive, even if it looks genuine. Question everything. Where did it come from? Am I expecting an email like this? In my case, I am not expecting any communication relating to a COVID test.
- If the email comes from someone you know, but the nature of the email is not something they would be likely to send you, call them. The chances are their system is infected with a virus that has attached itself to their address book and is sending emails to everyone in it, because they (the scammers) know you’re likely to trust the sender. Again, call the send first.
- Check the links without clicking them. Practice with links in known, trusted emails on your desktop/laptop and mobile devices so you become comfortable with checking their validity.
- Gut instinct. If you don’t trust it, don’t click it. If anything doesn’t look quite right, ignore it. If you can’t tell whether or not you trust it, ask someone else, preferably an IT support person.
- If you have no IT support, Google is your friend. A quick Google of the subject line will frequently reveal if it’s a scam. I discovered that a version of the scam email I received was originally reported by The Express, a UK tabloid newspaper, back in November 2020.
- Anti-virus/anti-malware software. Yes, it costs money, but do not underestimate the effectiveness of good anti-virus/anti-malware software for protecting you (and your family or company) against malicious attacks. Personally, I use [the brilliant] Bitdefender. A year’s subscription covers five devices and will stop 99% of malicious activity in its tracks. Others are available, but try not to be tempted by free software. Free is better than nothing at all, but it will never be as effective as a paid-for version.

An example of how easy it is to get caught out
Since email became the communication tool of choice, particularly in business, and even more so since the pandemic forced so many people to work from home, it’s all too easy to react to an email, especially if it either looks genuine or appears to originate from a source or contains information that feels familiar to you.
Familiarity is your worst enemy.
For example, you work in the accounts department and the company frequently uses FedEx courier services for product distribution.
One day you receive an email that looks like it came from FedEx with a FedEx email address, such as [email protected]. So far so good.
The email includes the FedEx logo, head office or local office address, full contact details and even a customer support telephone number. It looks, to all intents and purposes, to be completely genuine.
The message states simply that the invoice for your recent deliveries is attached. There is an attachment with a PDF icon, so you click to download the invoice so that you can process it.
Except it’s not a PDF. It’s a little piece of code known as ‘malware’ (like software, but really bad).
Clicking the icon doesn’t start the download process. You click again. You’re not sure what’s happening or why it’s not working. You ask a colleague. They suggest you click again. Maybe you forward the email to them and they click the icon. Nothing. You give up.
What’s actually happened is that your first click invoked the malware code in a split second and it infected your PC with a virus or some other malicious software bug. If you’re connected to a network, the malware will often rapidly work its way through the network to other PCs and will infect those too.
Chances are you’ll be unaware that anything has happened because the malicious code may sit on all the infected PCs for an hour, a day, a week, a month — or until a predetermined trigger occurs, such as restarting a PC. The malware could begin wreaking havoc across your system on all PCs, bringing the company to a grinding halt.

The world’s worst cyber attack
Possibly the worst example of a cyber attack that caused utter devastation around the world, was the Wanncry ransomware attack in 2017, where computers were automatically encrypted and could only be released for a fee.
According to the BBC’s report in May 2017, Europol stated that more than 200,000 computers in 150 countries were affected We know this number to be far higher now. The consequences were beyond anyone’s comprehension, and more than a year after the initial attack, the cost to the UK’s National Health Service alone in residual damage was more than £72m ($100m).
Don’t be the cause of something similar.
Be vigilant at all times. Be aware the scammers will use every trick in the book to convince you to click and/or complete a login form, or anything else they choose to try out on you. If you’re not sure; ask.

Originally published on clivewilson.com/marketing-insight/
About the Creator
Clive Wilson
I write with an inquiring mind about marketing, business and what life can teach us about life, and I take very little at face value.
You can find more about me at www.clivewilson.com






Comments
There are no comments for this story
Be the first to respond and start the conversation.