
Greetings to all! Here is a beginner practice CTF from Bsides Indore. The practice CTF will continue until May 2023. It is strongly recommended that beginners attempt this CTF to better understand the tools, methodologies, and learning concepts.
Visit: http://livectf.bsidesindore.in/
What is CTF?
A CTF refers to a game in which players make use of their skills in order to solve problems or break into the system of an opponent. Below are the different types of CTFs –
- Jeopardy style: Players are required to solve certain problems to earn "flags" (a specific string of text). The flag is then submitted to a website or scoring engine in exchange for points.
- Attack-defense: Two teams are created in this type of scenario: Red Team (which attempts to breach the system) and Blue Team (which seeks to defend the system).
Cryptography Challenges
1.BrainF**ked
The Cipher name is already included in the title of this challenge, which makes it very obvious. This challenge can be solved by below URL https://www.dcode.fr/brainfuck-language

2. Rotten Flag?
The name of the challenge gives a hint about Rot cipher, which is a simple character substitution that is based on the shift and rotation of N letters in an alphabet.
Use this to solve the above challenge https://www.dcode.fr/rot-cipher.
3. esrever

It looks like a reverse string, So we tried to reverse the given string by using this amazing online tool https://gchq.github.io/CyberChef/#recipe=Reverse('Character')&input=Cg
4. Dots and Dashes

Those who play CTF regularly can easily recognize this cipher as Morse code. Use this link https://www.boxentriq.com/code-breaking/morse-code to solve this challenge.
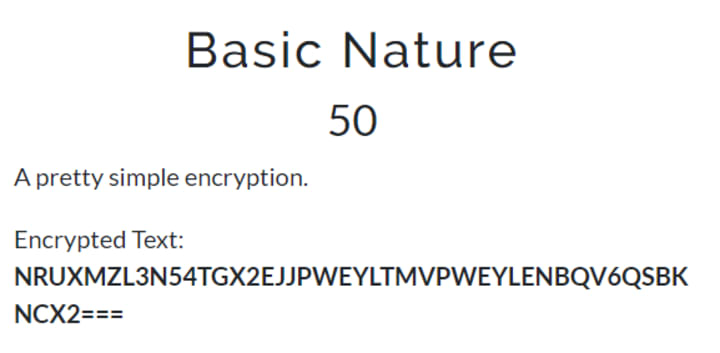
5. Basic Nature
In this challenge the string is given in base32 form, We have used cyberchef for decoding, We can also use this command for decoding
echo “NRUXMZL3N54TGX2EJJPWEYLTMVPWEYLENBQV6QSBKNCX2===” | base32 -d
6. Another Basic Nature?
This challenge is similar to the above one, Base64 is used on this challenge, using cyberchef, we can easily decode this.

7. Vinegar
In this given challenge, Vigenere Cipher is used, We can use the below link for solving this challenge https://www.dcode.fr/vigenere-cipher.

8. AK47
This challenge is all about ROT47, We have to use cyberchef https://gchq.github.io/CyberChef/#recipe=ROT47(47) for decoding.

9. Solve for PAT

The challenge presented here is quite interesting. In this challenge, we have provided a waterfromtap file attached in which we have found the following string.

The filename (waterfromtap) appears to be unknown, but if we analyze it properly, we find that it is related to tap encryption, so we have used it. https://cryptii.com/pipes/tap-code#:~:text=The%20tap%20code%20or%20knock,to%20communicate%20with%20each%20other. for solving the challenge.
In order to obtain the flag, We must convert the asterisk sign into a dot sign, then use the above-mentioned link.
10. World War II

In this challenge, If we analyze the description then we got the UKW C, If we google UKW C then we get to know that this challenge is regarding the enigma machine.
We need to use this link to solve the above challenge https://cryptii.com/pipes/P2CeCw.
11. Dev Lan What?
In this challenge, we have used this site https://www.devglan.com/online-tools/aes-encryption-decryption to decrypt the AES cipher.

Forensic Challenges
1. Elastic String
In this challenge we have given one attached image, We only need to use the strings tool for getting the flag.
Command: strings ctf.jpg

2. El As Bee

In this challenge we have been given a png image, So We have used the zsteg tool to find hidden data.
You can use this site https://github.com/zed-0xff/zsteg for downlode the zsteg tool.

It is that simple, folks!

Look forward to new CTF articles, so follow me on LinkedIn.
About the Creator
Samyakt
BYT3





Comments
There are no comments for this story
Be the first to respond and start the conversation.