Understanding Hashing Algorithm in Blockchain - A Comprehensive Guide
Dive into the world of the hashing algorithm in blockchain and discover its significance in securing digital transactions. Learn about the pros and cons of this crucial cryptographic technique. Read on to grasp the A to Z of hashing algorithm and its role in the blockchain ecosystem.
Introduction:
In the world of blockchain technology, hashing algorithm plays a crucial role in securing digital transactions. This comprehensive guide will provide a detailed understanding of hashing algorithm in blockchain, its inner workings, and its significance. From the basics of hashing to the pros and cons, we'll explore everything you need to know about this cryptographic technique.
Introduction to Hashing Algorithm
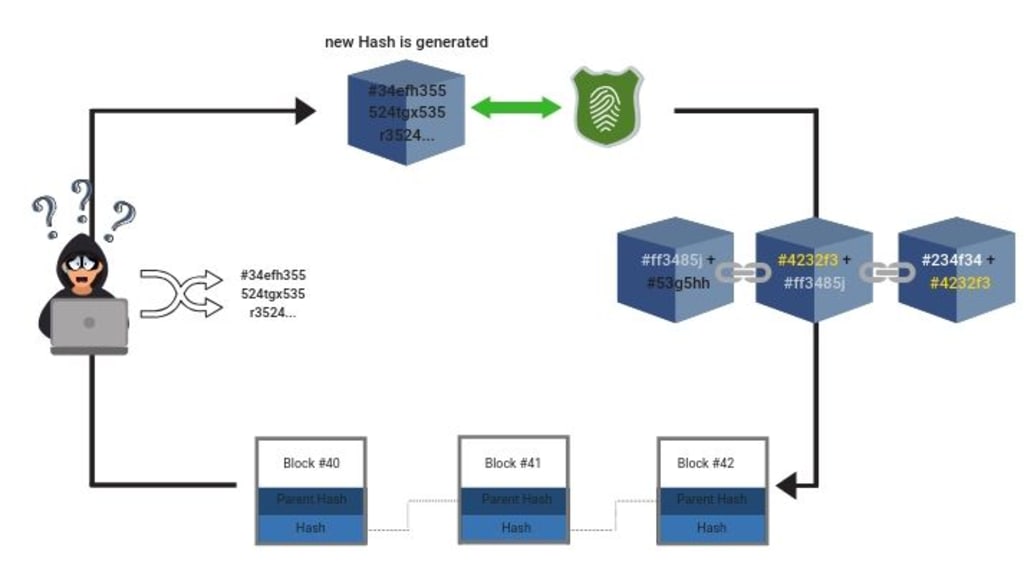
Hashing is the process of transforming an input, such as data or a message, into a fixed-size string of characters known as a hash. In blockchain, the hashing algorithm is a fundamental component that ensures the integrity and security of data stored on the distributed ledger. By using cryptographic hash functions, the blockchain prevents tampering with the data without detection.
The Hashing algorithm is designed to be deterministic, meaning that the same input will always produce the same output. It is also crucial to note that even a small change in the input will result in a completely different hash output. This property is known as the avalanche effect, and it plays a key role in ensuring the security and integrity of blockchain data.
How Does Hashing Algorithm Work?
Cryptographic hash functions are at the core of the hashing algorithm in blockchain. These functions take an input of any length and produce a fixed-size output. A good hash function possesses important properties such as determinism, pre-image resistance, collision resistance, and the avalanche effect.
Determinism ensures that the same input will always produce the same hash output. Pre-image resistance means that it is computationally infeasible to reverse-engineer the input from the hash output. Collision resistance ensures that it is highly improbable for two different inputs to produce the same hash output. The avalanche effect guarantees that even a small change in the input will result in a drastically different output.
In the context of blockchain, the hashing process involves taking the input data of a block, such as transaction details, timestamps, and the hash of the previous block, and applying a cryptographic hash function to generate a unique hash output. This hash becomes the digital fingerprint of the block and is used to verify the integrity of the data. Moreover, blockchain utilizes hash pointers and Merkle trees to efficiently store and validate large amounts of data.
The Pros of Hashing Algorithm in Blockchain
Hashing algorithm offers numerous benefits in the blockchain ecosystem. Firstly, it ensures data integrity and immutability. Any change in the input data will produce a different hash output, alerting the network to potential tampering attempts. The distributed nature of blockchain ensures that any alteration in a block's data will be detected and rejected by the network.
Furthermore, hashing enables efficient verification and validation of data. Instead of comparing the entire block or dataset, nodes can compare the hash outputs. This significantly reduces computational overhead and allows for faster and more efficient validation processes.
Collision resistance is another key advantage of hashing algorithm. The likelihood of two different inputs producing the same hash output is extremely low. This property minimizes the risk of data duplication or manipulation within the blockchain.
Scalability and performance benefits are also realized with hashing algorithm in the blockchain. Hash functions are designed to be computationally efficient, allowing for fast and efficient processing of data. As a result, blockchain networks can handle a large number of transactions per second, making them suitable for various applications.
In addition, hashing algorithm enhances the security and privacy of blockchain networks. As the input data is transformed into a fixed-size hash output, sensitive information is effectively obscured. This protects the privacy of participants and prevents the leakage of confidential data.
The Cons of Hashing Algorithm in Blockchain
While hashing algorithm brings significant advantages, it also has limitations that need to be considered. One concern is its vulnerability to brute-force attacks. In a brute-force attack, an attacker systematically tries different inputs to find a matching hash output. However, the strength of secure hash functions, such as SHA-256, makes brute-force attacks highly computationally intensive and impractical.
Another limitation is the dependency on computational power. As the complexity of hash functions increases, the computational resources required to generate the hash output also increase. This can pose challenges in resource-constrained environments or on devices with limited processing capabilities.
Moreover, there is a potential for pre-image attacks, where an attacker successfully generates an input that produces a desired hash output. While pre-image attacks are highly unlikely for secure hash functions, advancements in computing technology and cryptanalysis techniques may pose future threats.
In addition, the emergence of quantum computing poses a potential threat to the security of hashing algorithm in blockchain. Quantum computers have the potential to break certain cryptographic algorithms, including hash functions, rendering the existing infrastructure vulnerable. However, ongoing research in post-quantum cryptography aims to develop quantum-resistant hash functions and cryptographic primitives to address this concern.
Popular Hashing Algorithms in Blockchain
Several hashing algorithms are commonly used in blockchain networks. One widely adopted algorithm is SHA-256 (Secure Hash Algorithm 256-bit). It is extensively used in major cryptocurrencies like Bitcoin. SHA-256 provides a high level of security and has been battle-tested in the blockchain industry.
Other algorithms, such as Blake2, Keccak, Scrypt, and Ethash, are also utilized in different blockchain applications, offering varying levels of security and performance. These algorithms are carefully chosen based on the specific requirements and use cases of the blockchain network.
Use Cases and Applications of Hashing Algorithm in Blockchain
The applications of hashing algorithm in blockchain are diverse and wide-ranging. In cryptocurrency transactions, hashing algorithm ensures the integrity and immutability of transaction data, enabling secure and transparent digital payments. Hashing is also utilized in digital identity verification systems, where the hash of personal information is stored on the blockchain, allowing for secure authentication without revealing sensitive data.
Supply chain management is another area where hashing algorithm in blockchain finds significant use. By hashing product details, manufacturing information, and logistics data, blockchain can provide an immutable and transparent record of a product's journey, reducing fraud and ensuring authenticity.
Smart contracts and decentralized applications (DApps) rely on hashing algorithm for secure execution and validation. By using hash outputs to reference contract terms and conditions, blockchain networks can ensure the integrity of agreements and enable trustless interactions.
Future Developments and Advancements in Hashing Algorithm
The field of hashing algorithm is continuously evolving to address emerging challenges. Post-quantum cryptography aims to develop hash functions that are resistant to quantum computing attacks. Researchers are exploring novel hash functions with improved security and efficiency properties. Hybrid and adaptive hashing approaches, combining multiple hash functions, are also being explored to enhance the robustness of hashing algorithms.
Conclusion:
The Hashing algorithm is a vital component of blockchain technology, ensuring the security, integrity, and efficiency of digital transactions. By utilizing cryptographic hash functions, blockchain networks achieve data immutability, efficient verification, and enhanced privacy. While hashing algorithm offers numerous advantages, it is important to consider its limitations, such as vulnerability to brute-force attacks and the potential impact of quantum computing. As the blockchain ecosystem continues to evolve, hashing algorithms will adapt and innovate to meet the challenges of the future.
About the Creator
TeckyBlock
Learn about blockchain technology, cryptocurrency, NFT and metaverse in here. please visit https://teckyblock.com for further information.
Enjoyed the story? Support the Creator.
Subscribe for free to receive all their stories in your feed. You could also pledge your support or give them a one-off tip, letting them know you appreciate their work.






Comments
There are no comments for this story
Be the first to respond and start the conversation.