The Migration from Network Security to Secure Networks
Arista
The Migration from Network Security to Secure Networks
Over the last few years, we have seen an age of edgeless, multi-cloud, multi-device collaboration for hybrid work giving rise to a new network that transcends traditional perimeters. As hybrid work models gain precedence through the new network, organizations must address the cascading attack surface. Reactionary, bolt-on security measures are simply too tactical and expensive.
Shift to Zero Trust Networking
The perimeter of networks is changing and collapsing. This paradigm shift to a perimeter-less enterprise has prompted organizations to embed security into the network infrastructure as the proactive way to track and successfully manage threats coming in from the wider attack surface. However, historically it has been cumbersome to add multiple layers of network security with the consequential add-on hardware deployments, ongoing operational costs, and configuration changes needed at the network infrastructure level. Security teams have therefore been forced to the bare minimum network visibility.
Arista’s zero trust networking architecture focuses on baking security into the network by default rather than a bolt-on afterthought. Based on NIST 800-207, the Arista approach delivers situational awareness, continuous diagnostics, and zero trust enforcement.
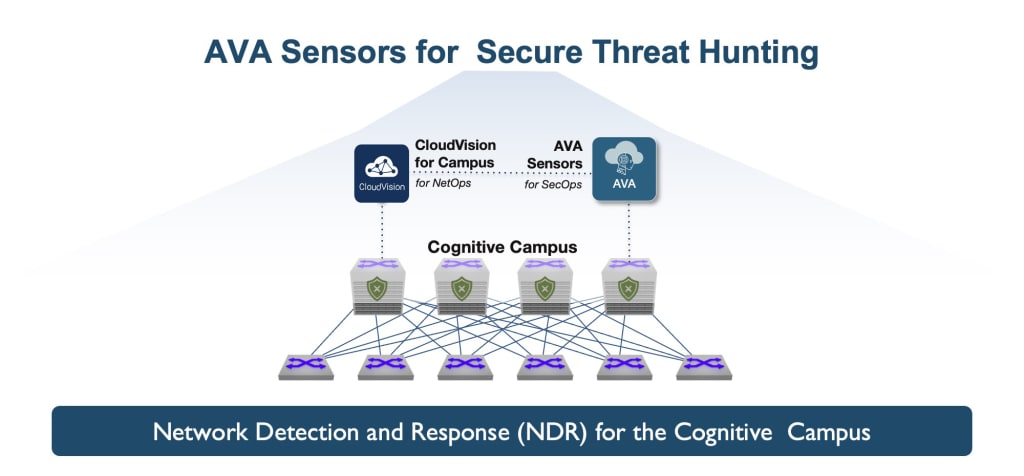
Arista AVA for High Fidelity Secure Networks
Arista AVA™(Autonomous Virtual Assist), derived from our Awake Security acquisition, is a pivotal component of zero trust networking. AVA imitates human expertise at a cloud scale through an AI-based expert system to automate complex tasks like troubleshooting and securing cyber threats. It starts with real-time, ground-truth data about the network devices' state and, if required, the raw packets. AVA uses an expert system to orchestrate an ensemble of AI/ML techniques on this data using supervised and unsupervised NLP (Natural Language Processing). Applying AVA to networking increases the fidelity and security of the network with autonomous network detection and response (NDR), bringing proactive security with enhanced efficacy and coverage.
Introducing AVA for the Cognitive Secure Campus
Traditional NetFlow-based solutions of the 1990s era are limited in their depth of visibility (port, IP address, and basic protocol information) and lack the context to identify modern devices or threats. In contrast, Arista NDR analyzes the full packet, including application layer data which sets the stage for automated and manual threat hunting.
For the first time, we are integrating Arista EOS-based campus switching and NDR functions. Powered by AVA, this AI-driven function has two key components: AVA Sensors and the AVA Nucleus. AVA Sensors support a variety of form factors from stand-alone appliances and virtual to cloud workloads and now, within campus power over ethernet (PoE) switches. These sensors curate and transfer the “just right” deep-packet data to the AVA Nucleus, offered as both on-premises and cloud Saas models. The AVA solution delivers persistent threat hunting with a simple switch software upgrade. This has minimal impact on switch performance or reliability and is transparent to the daily network switch operations.
The Time is Now
It is the right time to unify the network and security world for the secure cognitive experience. Security must permeate everything we do on the network today to bring a proactive and continuous approach to contextual monitoring and threat hunting. Lethal threats must be detected before proliferating to a massive data breach. Welcome to the zero trust networking era!





Comments
There are no comments for this story
Be the first to respond and start the conversation.