Use Email Security Tools to Protect Remote Employees and Data
Organizations must understand that to secure their money and data, it is inevitable that they need to set up email authentication protocols. However, email authentication can be tricky and complicated.
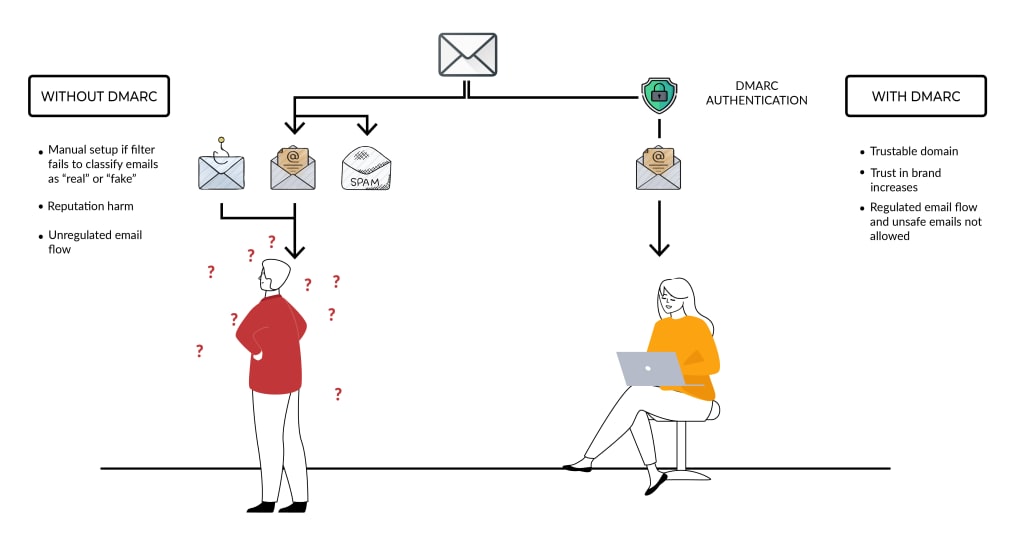
Organizations must understand that to secure their money and data, it is inevitable that they need to set up email authentication protocols. However, email authentication can be tricky and complicated.
DKIM, SPF, and DMARC are the three protocols available for email authentication that ensure better email deliverability and email security. Let’s understand the differences between these protocols and how each of them authenticates emails.
SPF allows domain owners to specify which addresses are authorized to send emails on their behalf. DKIM, on the other hand, uses an encrypted signature to verify if an email sender is exactly who they claim to be. Both these technologies produce individual authentication identifiers that help authenticate and validate emails and their senders. If you have implemented these protocols, receiving servers are able to identify who an email is from but do not know if your traffic is properly configured. Therefore, they cannot take proper and efficient action against emails that fail authentication.
DMARC combines the results of SPF and DKIM to accurately identify if an email is from an authorized sender or a fraudulent impersonator. As a result, it is able to actively block cyberattacks by enforcing the policy specified by the domain owner. That’s right! With DMARC, domain owners can instruct receiving servers on how to deal with emails using their domain by implementing a DMARC policy of their choosing.
Let’s dive deep and look into the protocols singularly:
DKIM or DomainKeys Identified Mail is an anti-tamper protocol that ensures the security of emails in transit. This protocol uses digital signatures to check whether the email was sent by a specific domain.
DKIM uses two actions to validate your messages. The first action occurs on a server sending DKIM signed emails, while the second takes place on a recipient server checking DKIM signatures on incoming messages. The entire process is made possible by a private and public key pair. The private key is kept secret and safe either on your server or with your ESP. The public key is added to the DNS records of your domain to broadcast to the world and help verify emails. This is done by providing a digital signature for all emails sent by a server that has DKIM configured.
Once the receiver verifies that an email is signed with a valid DKIM signature, it’s clear that the integrity of the email is preserved. Usually, end-users cannot see DKIM signatures; the validation is done at the server level. The DKIM standard helps to improve email deliverability.
SPF
SPF or Sender Policy Framework is an email authentication protocol that allows domain owners to specify which email servers are permitted to send email from their domain(s).
SPF detects forged sender addresses while the email is being delivered. It allows the recipient mail server to verify whether emails claiming to come from a given domain have indeed been sent from an IP address authorized by the domain's administrators.
Messages sent from your company or domain that do not include SPF are more likely to be flagged as spam by recipient mail servers. Therefore, it is recommended that you set up DKIM and DMARC in addition to SPF. These authentication techniques increase the security of your domain and ensure that messages sent from it are delivered correctly.
Now that we have a better understanding of SPF and DKIM and how they ensure the sanctity and legitimacy of outbound emails, let's see how DMARC works in alignment with both protocols to prevent spoofing, phishing, and other email-based cyberattacks.
DMARC (Domain Based Message Authentication, Reporting and Conformance) is an email authentication standard or protocol that determines whether an email is authentic or not. It relies on SPF and DKIM, two other protocols, to decide the authentication status of the email. It provides visibility of the original source of the email and not just the domain it claims to be from. DMARC ensures better deliverability, provides top-notch email security and ensures that your domain does not fall prey to spoofing attempts, phishing scams, and impersonation attacks.
Phishing attacks led to an estimated $1.9 billion in losses in 2020. Organizations worldwide suffered major data breaches and spoofing attacks in the last couple of years. Data and money that is lost after a major cyberattack are irrecoverable in most cases. Hence, it is of utmost importance that brands set up stringent email protocols to better protect their critical assets.
Here are a few advantages that SPF, DKIM, and DMARC protocols offer:
1. Using a DMARC record prevents unauthenticated parties from sending messages using your domain. This secures your reputation as customers will be sure that emails sent by your organization’s domain are authentic.
2. DMARC and its policies build a steady strategy for managing emails that fail the authentication test. This makes your email channels safer and more reliable.
3. DMARC, DKIM, and SPF allow you to use the same email authentication technologies and strategies that large companies use to deliver and secure their email channels.
4. SPF improves email deliverability and security while fighting domain impersonation that could severely tarnish your brand reputation.
To Know More About:- Email Deliverability and Domain Reputation
5. DKIM helps identify emails that aren’t known to be spam and don't need to be filtered. If a receiving system maintains a whitelist of authentic sending domains, which can be kept locally or obtained from third-party certifiers, it can skip the filtering of signed mail from those domains and filter the remaining mail more aggressively.
It is shocking that despite the prevalent threats in the current digital era and the evident effectiveness of these protocols, around 80% of the organizations worldwide haven’t adopted DMARC. To get rid of spoofing and phishing attacks intended to steal money and data, every brand is advised to implement these protocols and fend off the malicious cyberattacks. Organizations stand to save millions by just strengthening their security protocols and implementing email authentication protocols.
Original source: https://www.idg.com.au/mediareleases/204841/use-email-security-tools-to-protect-remote/




Comments
There are no comments for this story
Be the first to respond and start the conversation.