Reduce Cybersecurity Risks to Keep Your Critical Data Safe
The age of the Internet brings with it an exponential increase in the value of data.

Data is quickly becoming an increasingly more valuable asset as companies and individuals have entered into the era of external data-harvesting.
More storage of our information is digital than physical. Our data lives on servers owned by others including our name, date of birth, pictures, and address.
Technology tries to keep up with protecting our personal information, but at times it is an uphill battle. We give away our data willingly to access information such as services, news, and applications.
As all high-value assets, data is vulnerable. There are various stages in the life cycle of data where breaches can occur.
What is the Data Life Cycle?
The life cycle of data refers to the stages or general process that describes how it flows. The specific cycle will depend upon where and for what purpose the data is collected. The general flow is as follows:
- Initial capture, collection, or generation
- How the data is processed and maintained
- The active phase that uses data to support its objective
- In some cases, our information resides outside of where it was collected such as in an organization
- The archiving phase is when data is no longer processed, used, or published but stored for possible future use
- The final phase is purging when the data is deleted
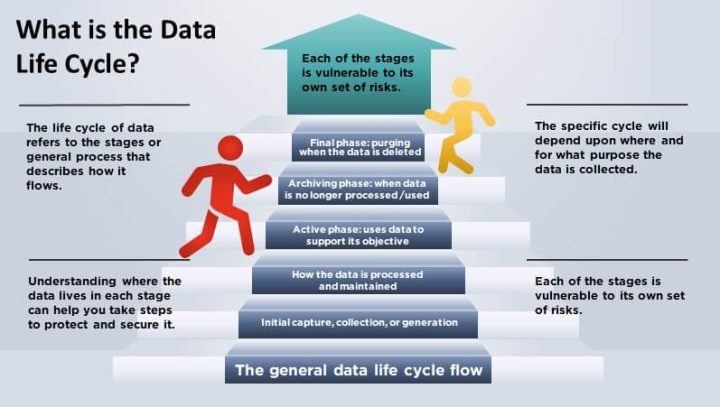
Each of the above stages is vulnerable to its own set of risks. Understanding where the data lives in each stage can help you take steps to protect and secure it.
Who Are the Victims of Data Breaches?
The media regularly report about security exploits and data breaches ranging from small companies to large global organizations.
In 2018, Intent and Engagement (IDG) released a study on the state of cybercrimes. It underscored the reality that companies of all sizes face the challenge of finding effective ways to protect critical IT infrastructure and data from cybersecurity threats.
Think about some of the national headlines from 2018 of famous brands suffering cybersecurity breaches:
- Facebook exposed personal data of almost 50 million users
- Reddit suffered a security breach that enabled hackers to bypass Reddit’s text message two-factor authentication security
- Delta Airlines’ customer data was compromised by a third-party online chat service provider
- FedEx exposed sensitive customer data from an unsecured Amazon S3 server
The takeaway from these high-profile breaches and the number of individuals affected by them is that cybersecurity risks are a harsh reality that must be addressed.
The complex, multi-dimensional, and interconnected nature of IT infrastructures leave multiple back doors and intrusion points for hackers to exploit.
The negative consequences for larger businesses vary depending upon the type and breadth of the breach. They include financial losses, legal penalties, and reputation damage.
What Can You Do?
Whether you are an individual, small business, or large organization, there are steps you can take to mitigate data breach risks and thwart hackers.

The scope of activities is vast, ranging from small changes to overall organizational changes. When followed, some of the basic rules and practices can empower companies and individuals to reduce exposure to cybersecurity risks to protect sensitive data.
Use Anti-Virus Protection Software
Anti-virus software recognizes malicious threats and protects your computer against it. The United States government recommends visiting vendor sites directly rather than clicking on a link in an ad or email because they may contain viruses, infections, or malware.
Keep your anti-virus software up to date. The better products are updated frequently to fix security exploits and ensure systems are as effective and safe as possible against threats.
If a virus is detected, the software program will intercept and quarantine the threat to prevent it from further infection and spreading.
Adequately Encrypt Your Important Data
Encrypted data prevents others from accessing and reading it should a security breach occur.
We have all heard that VPN services (Virtual Private Networks) are one of the best ways to protect data on the Internet.
A VPN is a series of virtual connections that encrypts undecipherable data as it travels back and forth over the Internet.
However, not all VPNs are created equal. Different VPNs use different technologies and encryption standards.
Which VPN service you choose depends upon your needs. Some of the critical categories that differentiate them include:
- Stability
- Speed
- Customer service
- Privacy
- Anonymity
- Additional features
- Pricing
Using servers with outdated versions of encryption, SSL, or systems that have expired certificates will increase the chances of privacy and security breaches.
Utilize Multi-Factor Authentication (MFA)
MFA adds one or more additional requirements necessary for access to data. It is a secure tool to help mitigate cybersecurity risks.
Retina scans, fingerprints, a biometric signature, or something else unique to an individual are required by users to gain access.
Back Up Critical Data
Although backing up your data won’t help get privacy or sensitive information out of the hands of malicious actors, it can at least prevent data loss.
Organizations must have a proven backup strategy to create copies to roll back in case of disastrous incidents.
Secure Your Infrastructure
Technical solutions exist that can harden a company against cybersecurity threats. Some organizations outsource their IT department to a managed service provider to manage and secure their entire IT infrastructure.
If you outsource your IT or keep your systems in-house, be sure to monitor network traffic for suspicious activity regularly.
Choose from several platforms that will monitor your infrastructure, generate reports on system performance, and track and monitor user and system behavior.
Frequent scanning will help organizations understand where their sensitive data is stored. Ideally, the storage solution should be encrypted and restrict access to it. Only the right people should have permission for access.
Use a Holistic Ongoing Approach
After a breach has occurred, quickly executing reactive measures to restore a backup of your critical data can’t undo the damage.
Security risks and malicious attacks continue to be a significant threat. Data security best practices advance to protect against novel hacking techniques and the latest exploits.
The only way to adequately safeguard data is to plan correctly, frequently monitor, and assess and measure information security programs.
Even the most robust security management will develop exploitable weaknesses. Remain vigilant to the vulnerability of data from malicious data breaches.
About the Creator
Julie Weishaar
Julie works to grow small businesses, increasing their online visibility by leveraging the latest in internet & video technologies. She specializes in animated video production, custom images, content writing, and SlideShare presentations.






Comments
There are no comments for this story
Be the first to respond and start the conversation.