Implement JWT Token in 9 Minutes
Learn to implement JWT web token with your Java project quickly.

I am writing this article to focus on what is JSON Web Tokens (JWT), What are the pros and cons of using them, and how you can implement them easily with any java framework (like Spring, Spring boot, etc.) without any hurdles.
Java keeps up supporting the new ideas as always, And so JWT (JSON Web Tokens) is also a new step for OAuth Protocol— Mostly JWT can be used in Hybrid Applications like NG 2+ (Angular framework) as a Frontend and Java 8+ as a Backend. IT Industries are also using VueJs and Java or React and Java combination. Which is trending nowadays.
I saw that most of all developers are using the JWT Token for their Java and Android projects because of its own benefits! Moreover, IT Industry people are using Hybrid applications, let’s say for example Angular/ ReactJS/ VueJS as frontend, Java/ .Net/ Php as backend, hence there might be a possibility for multiple backends (i.e. Bifurcate into separate micro-service authentication servers, DBS, video hosting servers, image processing servers, etc.). For these situations, the session cookie we get from one server won’t correlate with another server. It will be stay separated always.
Benefits of using JWT Tokens
- Its Portability, the major reason for its popularity: A single token can be used with a number of backends. For example, Use it for restful APIs or restful clients, create generic third-party libraries, and web MVC applications — so others can also consume your web services, if any requirements match with that.
- SuperDuper productivity: It reduces the network round trip time and so it will increase better performance compatibility.
- It is stateless, Give session management accountability to itself: The JWT is a form of the token itself that holds authentication data, expiration time information, and other user-defined claims which are digitally signed.
- Session Cookies are outdated, Use JWT (JSON Web Tokens) instead.
- No more dependent: It is decentralized, we can say, it is “loosely coupled“. The token can be generated from anywhere. Auth can take place on the resource server or easily separated into its own server.
- Mostly applicable for micro-services structure: Instead of making a session and setting a cookie, the server will send you a JSON Web Token instead. It will do session management work for you with fewer efforts.
What Are JWTs?
JWTs are an encoded depiction of the JSON object. This JSON object consists of 0 or maybe more key/value pairs, where the keys are strings and the values are arbitrary JSON values. JWT is helpful while sending such data in a simpler way (for example, in an URL) while it can still be trusted to be unmodifiable (because it’s signed), unreadable (because it’s encrypted), and URL-safe (because it’s Base64 encoded).
JWTs can be used in different ways, let me give you few examples of that. You can use it in the authentication mechanisms, interoperability, data expiration, URL-safe encoding, securely sharing private data, etc. Regardless of how you will use your JWT, the mechanisms to construct and verify it are remaining the same. So, let’s see how we can very easily achieve authentication and verification with the JSON Web Token for Java projects.
Generate JWT Tokens:
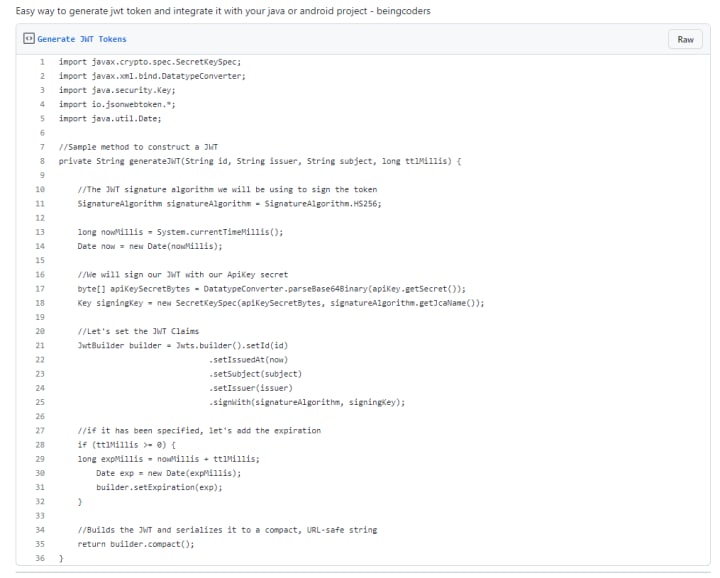
Parse and Verify JWT Tokens:

Why We Need Token-Based Authentication System?
These token-based authentication systems (JWTs) allow users to enter their username and password in order to obtain a token which allows them to fetch specific data sending their username and password for each request. Once their token has been obtained, the user can use the token to access specific data for a set time period. (Until it expires after a given time period)
JWT (pronounced ‘jot’) is a token-based authentication system. JWTs are smaller in size, URL-safe means of depicting claims to be transferred between two parties. If you observed, the claims in a JWT token are encoded as a JSON object, which was digitally signed using JSON Web Signature Module. The JWT contains a token that has authentication data, expiration time, and other user-defined claims digitally signed.
Reference:
Get my stories in your feeds by subscribing to me, or become a vocal+ member to read all stories of thousands of other writers, participate in all challenges and get a payout with low fees and less payout threshold on Vocal Media.
© Originally published at JWT Integration Java, also republished on Medium by Rakshit Shah
About the Creator
Rakshit Shah
I am Computer Engineer and love to make websites and software. I am really eager to know about anything. I am curious to read and write cool stuff.






Comments
There are no comments for this story
Be the first to respond and start the conversation.