Image Steganalysis in Digital Forensics
Secure communication is a fundamental need of today’s digital world because development of digital communication.

Abstract— Steganography and steganalysis is a relatively new-fangled scientific discipline in security systems and digital forensics, respectively, but one that has matured greatly over the past two decades. In any specialism of human endeavor, it is imperative to periodically pause and review the state of the discipline for what has been achieved till date. This article scrutinizes where the discipline of steganography and steganalysis at this point in time in context to the common user and new researchers in terms of current trends. This paper is intended to provide a complete guide for common people and new researchers and scholars approaching this field, sight on the existing and the future of steganography and steganalysis.
Keywords- Cybersecurity. Digital forensics. Steganography. Steganalysis. Tools
Introduction
Secure communication is a fundamental need of today's digital world because development of digital communication. Steganography is a covert communication art in which information is concealed in a cover object. With the advent of computer systems, today new opportunities and new places to hide confidential data have developed [1]. Today, steganography is now accessible and within the reach of ordinary people for covert communication using their own systems or even cell phones with an internet connection. In addition to information hiding, there are other secure communication techniques such as cryptography and watermarking. However, steganography has advantages over cryptography and watermarking, i.e. the steganography medium after embedding seems to be the same as the overlay medium (in which the data is masked). The joint use of cryptography and hiding techniques can effectively develop secret communication techniques. Watermarking is another area of information security that aims to focus on copyright and infringement protection. Watermarking data hiding can be done in a similar way to steganography. Although there are similarities in embedding, there are some differences between watermarking and hiding techniques [2]. One of the main differences is that in steganography, the embedded message will always be hidden, whereas, in the case of watermarking, the messages can sometimes be seen as well [3]. Furthermore, the main goal of steganography is to disguise the message in the covered object in such a way that it cannot be recognized by an intruder; The main purpose of a watermark is to embed data in the cover object in such a way that an intruder cannot detach or overwrite that data. Steganography is necessary for secure communication in various fields such as banking, army, etc. and even by ordinary people, will be discussed in detail in the application section of this article. The reason for the prevalence of data archiving techniques is not only because of its ethical practices but also because of some unscrupulous practices, such as embedding viruses, spam and malicious links. to the data of cybercriminals. Even terrorists have used cryptography for their illegal motives and sabotage. Thus, over the past decade, rapid developments in the field of steganography and stegananalysis have attracted people from all field.
Steganography
Communicating and storing stable records has come to be part of everyday lifestyles for everyone; both it's miles a safety professional or not unusual place people. Steganography performs a vital position in supplying safety for verbal exchange and storing mystery records/statistics. The goal of steganography is to embed a awesome mystery message right into a cowl item which may be something to be transferred over the net consisting of images, text, audio, PDF files, films etc. Due to the ever-growing cyber-crime, the safety of private records/statistics is one of the primary necessities of private well-being.
Steganography may be utilized in distinct regions relying upon the kind of carrier. With the technological advancements, steganography traits have additionally been advanced, and a number of the contemporary traits of steganography include- multimedia, files, network, Skype, clinical images, DNA etc. The huge categorization of the contemporary steganography traits is proven in Fig. 1
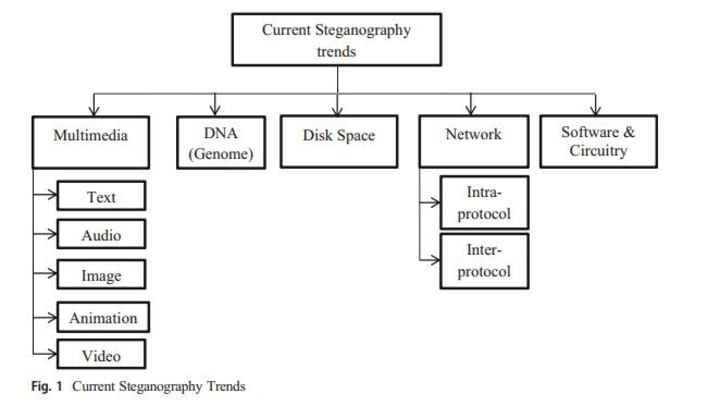
Multimedia steganography- It consists of hiding mystery records internal any multimedia documents without difficulty with none seen distortion. There exist several studies articles at the image, audio and video steganography wherein records are hidden the use of specific strategies which includes spatial and remodel domain-primarily based totally strategies [4].
DNA (Genome)- DNA (Deoxyribonucleic acid) steganography is likewise referred to as Genome steganography. In Genome steganography, the message is encrypted and located among primers, which can be the place to begin of DNA synthesis and further, mystery records are hidden in a microdot [5].
Disk Space - This type of steganography allows hidden data in free disk space plate. Sometimes secret data is hidden in the disk's logical channels using unused and redundant fields, which are not obvious to network professionals and
forensic pathologist. Example: Master Boot Record (MBR) of unbootable hard drive and free disk space due to misalignment of hard drive files and industry scale [6].
Network steganography - This is a relatively new field of steganography where data is hidden using redundant communication mechanisms. It can be assumed that it creates hidden communication channels using protocols such as TCP, IP, UDP, etc. to mask the data. As a result, network steganography can be classified into two parts - intraprotocol steganography and interprotocol steganography. Data mask the use of Skype is also done using network hiding techniques [7].
Software and Circuits - Another area of cloaking where data can be concealed is software and system circuits. Steganography software to hide data in code program layout and the like, in the layout of electronic circuits, data can be hidden [8].
1.1 Real-time applications of steganography
In the realm of internet secure data transmission is the aim of almost all the fields in communication which could be achieved by concealing the data inside some common media. Steganography has its application in most of the common fields such as military, medical, corporate and multimedia where covert communication may be needed for some internal and external security purposes.
1) Military- In military and defense field secure message transfer is the primary aim of communication. Steganography has been widely used for this purpose since long by military persons for covert communication as common transmission channels may be conceded [17]. Authorized communication in military and defense is the base of their communication systems. In military and defense, additional multiple layered securities are also provided by using different encryption schemes before embedding the secret data.
2) Intelligence Agencies- Communication in intelligence agencies are also covert most of the times and steganography has been widely used for the camouflage [18]. National Security Agencies (NSA) has been using steganography to transfer secret message within and outside the agency.
3) Medical- Steganography has been used in the field of medical sciences by employing image steganography in medical images used for diagnosis such as CT, MRI etc. [19] It is used to hide the crucial private information of the patient diagnosed in the medical image itself. Further, in medical sciences, a sequence of DNA has also been used to hide secret information [20, 21]. This is usually done to secure the patient’s data and to avoid any leakage of private information from some unauthorized person/party.
4) Multimedia- In multimedia applications, steganography is frequently employed for watermarking used for copyright information marking [22]. This is done to verify and save the media such as images, movies etc. from illegal copying and infringements.
5) Smart IDs- Nowadays steganography has also been used for hiding the details of individuals in their photograph in smart ID.
6) Corporate- In corporate and industry communication, data leakage is the most menacing thing for a business. Therefore, the secure communication using steganography is always appreciated for security and authenticity as sometimes unsafe communication may lead to serious data breach [23].
1.2 Image steganography techniques
There are different ways to classify the imaging techniques that researchers have used in their investigative papers [9,10,11] some common classifications are based on domain, recovery" reversible or irreversible"; In general, image hiding techniques can be classified according to their domain: spatial and transform domain. Furthermore, some researchers have developed adaptive steganography techniques using different fields such as object detection and artificial intelligence [12]. However, these techniques can also be used for reverse and irreversible copy recording techniques. The basic steps involved in the steganography (image) technique are shown in the Fig. 2

Fig2. Basic block diagram of image steganography process
i) Spatial domain technique
Spatial domain-based image steganography is achieved by manipulating pixel values directly to embed secret data. The main advantage of spatial domain techniques is that it is easy and fast to deploy, making it the most used domain for hiding techniques [11]. There are different spatial domain techniques for image recording such as least significant bit (LSB), palette based, pixel value discrimination (PVD), bit plane based techniques, expression shift, etc. stuff, etc. The most commonly used technique for hiding information in the spatial domain is embedding in LSB (Least significant bit).
ii) Transform domain techniques
In the transform domain, integration is performed in the transformed coefficients rather than directly at the magnitude values. There are several different transform domain methods that have been used by researchers to capture hidden images, including Discrete Fourier Transform (DFT), Discrete Cosine Transform (DCT), and Discrete wavelet transform (DWT).
iii) Adaptive Steganography techniques
Adaptive image steganography methods are designed to target specific regions or pixels of the cover image to embed confidential data to improve the efficiency of image duplication techniques. This includes several methods such as targeting the human visual system (HVS) embedding to improve imperceptibility [13], using threshold values [14], or merging other domains to improve the basic requirements of high-security imaging techniques.
Steganalysis
Steganalysis is the art of detecting hidden information embedded in the use tool or technique to hide in media files. The need for data analytics in the digital world forensics first emerged after 1983 when, at the National Center for Computer Security (NCSC), theoretical threats from hidden vehicles were discussed [15]. The primary goal of the forensic data analyst is to detect and extract or recover hidden information if it exists in the communication reliably [16]. In cloaking, if masking subjects are chosen appropriately and correctly, even unimportant techniques can be concealed for a long time. What's worse, from a cyber/legal expert's point of view, is the number of tools and techniques available to conceal confidential data, even for the average person. On the other hand, the challenge for the forensic examiner is to distinguish hidden data in cover-ups and extract confidential data for counterterrorism and national security purposes. The steganalysis process requires knowledge of the original media, which is not available in most cases. Steganalysis is performed using the features and characteristics of the stego- and the cover object. It's easy to analyze data against a particular data logging technique or tool because it targets some specific feature just for detection. Although it is possible to develop a fairly good hiding analysis tool/technique for a targeted hiding tool/technique, however, it is very difficult. Design a common framework or layer of hiding techniques. The long-term goal of forensic pathologists should be to design and develop a data analysis technique or tool for all types of hidden imaging techniques.
In the digital world, image and video analysis is still an emerging area in the field of digital forensics, which is an important inference to ensure the integrity of digital media on the Internet. Worryingly, we are faced with a huge number of images and videos every day, and among them, at least some of them must be embedded with confidential data for cyber fraud or any other crime.
2.1 Image Steganalysis techniques
Image Steganalysis has come a long way from typical machine learning algorithms where manually extracted features into automatic deep learning feature extraction algorithms. This section has discussed some of the most advanced image analysis techniques with their comparative analysis, from machine learning to deep learning-based techniques.
Machine learning based techniques
Machine learning techniques are widely used in image steganalysis to automatically detect and analyze the presence of hidden information within digital images. The main idea behind using machine learning in steganalysis is to train a model to recognize the characteristic features that are indicative of the presence of steganography in an image. Here's how machine learning techniques use image steganalysis:
a) Supervised learning: In this approach, a machine learning model is trained on a large labeled dataset of images, some of which contain hidden information and others that do not. The model is then used to classify new images as either containing steganography or not.
b) Unsupervised learning: In this approach, the model is trained on an unlabeled dataset of images and tries to identify the anomalies and patterns within the data that are indicative of the presence of steganography.
c) Deep learning: In image steganalysis, deep learning models can be trained on large datasets of images to learn how to recognize subtle changes in pixel values that indicate the presence of hidden information.
d) Ensemble learning: In this approach, multiple machine learning models are combined to make a more accurate prediction about the presence of steganography in an image. These machine learning techniques use image steganalysis by analyzing the image data and extracting features that are indicative of the presence of hidden information. The models then use this information to make predictions about the image, allowing the steganalysis process to be automated and more efficient.
Deep learning based techniques
Deep learning-based techniques are widely used in image steganalysis to detect the presence of hidden information in an image. This is achieved by training deep neural networks on large datasets of cover and stego images. The neural network is designed to learn the statistical differences between cover and stego images and use this information to classify new images as either cover or stego. The network is trained using supervised learning, where the network is fed labeled training data and uses this information to optimize its weights and biases. The network can then be used to perform steganalysis on new images by passing them through the network and analyzing the output. These techniques have shown promising results in detecting steganography in images and are becoming increasingly popular for use in digital forensics and security applications.
Experimental results and discussion
As an experimental example, utilized one of the most common steganography tool “OpenPuff” to embed secret data inside an image of PNG format with dimensions 1920 × 1080. The reason behind choosing this tool is that it utilized multi-layered data obfuscation to provide additional security and more protection as it uses three passwords. Fig. 3 (a) shows the cover image and resulted stego image (Fig. 3 (b)) after using embedding secret data using OpenPuff. It is evident from the figure that both the images are same without any visual distortion. However, after further processing for steganalysis which is done by using Hex Editor Neo (freeware) it can be clearly perceptible that after embedding there is difference in the hex values as shown in Fig. 3 (c) and (d).
Additionally, the basic LSB based embedding has been done in an image of size 560 × 438 and secret image of the same size has been embedded using last 2 bits modification. The visual results of the cover and stego-image are shown in Fig. 4(a) and (b), again for steganalysis again Hex Editor Neo has been used and the results of steganalysis is shown in Fig. 4 (c) and (d) for cover-and stego-image respectively. It can be seen from the Fig. 4 that initial values have no difference; however, after 5th line it shows clear difference between the hex values which are highlighted in the Fig. 4(c) and (d).

Fig. 3 a Cover image, b Stego image after embedding using OpenPuff steganography tool; and hex values of c cover image and d stego image using Hex Editor Neo

Fig. 4 a Cover image, b Stego image after embedding using 2LSB steganography technique; and hex values of c cover image and d stego image using Hex Editor Neo
Conclusion
This paper is intended for the general public and new researchers interested in this field. Steganography and steganalysis. The focus of this work was to provide a basic guide for the study and application of steganography and steganalysis. Real-world use cases of steganography by criminals and terrorists were also discussed from the perspective of forensic investigators and cyber experts. This research aims to provide a complete guide to the general public and new researchers and scholars working in this field and to examine the existence and future of steganography and steganalysis.
VI. References
Warkentin M, Bekkering E, Schmidt MB (2008) Steganography: Forensic, Security, and Legal Issues. J. Digit. Forensics, Secur. Law JDFSL 3(2):17
Dalal M, Juneja M (2019) A robust and imperceptible steganography technique for SD and HD videos. Multimed Tools Appl 78(5):5769–5789.
Mousavi SM, Naghsh A, Abu-Bakar SAR (2014) Watermarking techniques used in medical images: a survey. J Digit Imaging 27(6):714–729
M Dalal and M Juneja (2018). “Video Steganography Techniques in Spatial Domain-A Survey,” in Proceedings of the International Conference on Computing and Communication Systems, Springer, Singapore, pp. 705–711
Z Wang, X Zhao, H Wang, and G Cui (2013). “Information hiding based on DNA steganography,” in 2013 IEEE 4th International Conference on Software Engineering and Service Science, pp. 946–949
Khan H, Javed M, Khayam SA, Mirza F (2011) Designing a cluster-based covert channel to evade disk investigation and forensics. Comput Secur 30(1):35–49.
W Mazurczyk, M Karas, and K Szczypiorski (2013). “SkyDe: a Skype-based steganographic method,” arXiv Prepr. arXiv1301.3632
NF Johnson, Z Duric, and S Jajodia (2001). Information Hiding: Steganography and WatermarkingAttacks and Countermeasures: Steganography and Watermarking: Attacks and Countermeasures, vol. 1. Springer Science & Business Media
Cheddad A, Condell J, Curran K, Mc Kevitt P (2010) Digital image steganography: survey and analysis of current methods. Signal Process 90(3):727–752
Swain G (2016) A steganographic method combining LSB substitution and PVD in a block. Procedia Comput Sci 85:39–44
M Hussain, AWA Wahab, YI Bin Idris, ATS Ho, and K-H Jung (2018). “Image steganography in spatial domain: a survey,” Signal Process. Image Commun
Kim J, Park H, Park J-I (2020) CNN-based image steganalysis using additional data embedding. Multimed Tools Appl 79(1–2):1355–1372
Luo T, Jiang G, Yu M, Xu H, Gao W (2018) Sparse recovery based reversible data hiding method using the human visual system. Multimed Tools Appl 77(15):19027–19050
Xue Y, Liu W, Lu W, Yeung Y, Liu X, Liu H (2019) Efficient halftone image steganography based on dispersion degree optimization. J Real-Time Image Process 16(3):601–609
Patel A, Shah M, Chandramouli R, Subbalakshmi KP (2007) Covert channel forensics on the internet: issues, approaches, and experiences. IJ Netw Secur 5(1):41–50
Rocha A, Scheirer W, Boult T, Goldenstein S (2011) Vision of the unseen: Current trends and challenges in digital image and video forensics. ACM Comput. Surv 43(4):26
Jamil T (1999) Steganography: the art of hiding information in plain sight. IEEE potentials 18(1):10–12
Mercuri RT (2004) The many colors of multimedia security. Commun ACM 47(12):25–29
Balu S, Babu CNK, Amudha K (2018) Secure and efficient data transmission by video steganography in medical imaging system. Clust Comput:1–7
FC Bancroft and C Clelland (2001). “DNA-based steganography.” Google Patents
MRN Torkaman, P Nikfard, NS Kazazi, MR Abbasy, and SF Tabatabaiee (2011). “Improving hybrid cryptosystems with DNA steganography,” in International Conference on Digital Enterprise and Information Systems, pp. 42–52
Katzenbeisser S, Petitcolas FAP (2000) Digital Watermarking. Artech House, London
Kadhim IJ, Premaratne P, Vial PJ, Halloran B (2019) Comprehensive survey of image steganography: techniques, evaluations, and trends in future research. Neurocomputing 335:299–326
Launched to the world in 2017, Wisemonkeys is now a robust Learning management system.
Just follow a 3-step registration process and get connected. Since we appreciate genuine users and do not encourage spammers we follow a small registration process:
2. Confirm your email. (for the first time the email might fall into your spam/junk/promotion folder. Please mark it as not spam and confirm the link).
3. Login and get started.
4. Or log in via Google/Microsoft.
Our hardworking team is thriving hard to make this platform better and better. If you have any suggestions and feedback, then do write to us at: [email protected]





Comments
wise monkeys is not accepting comments at the moment
Want to show your support? Send them a one-off tip.