How to Secure Your Gmail Account
You wouldn't like someone snooping around your Gmail account, would you? I can't blame you. Lock it down right now.

Gmail is the most popular free email service used by millions of people around the world. Billions of messages are sent and received through Google's email software each day. Many of these messages contain personal or confidential information.
From bank statements to personal letters, and even password reset requests, your Gmail account holds an abundance of personal information. If someone were to access it, they'd effectively have access to the rest of your online identity.
Instead of just hoping that hackers don't find you, take 10 minutes and secure your Gmail account right now.
Use a strong password--
Having a weak password like “password” is not as safe as you would think. A simple SQL injection attack or a brute force attack can easily get your password. It is recommended that you keep a unique and strong password for your account.
Use unique, randomly generated passwords, for every online account you have. Keeping track of all those passwords is easy when you use a password manager.
To change your Google account password, visit the Google account security page and click on Password under the Signing in to Google section. Verify your password if prompted, then enter your new password -- generated by your password manager -- and click Change password.
Enable two-step verification--
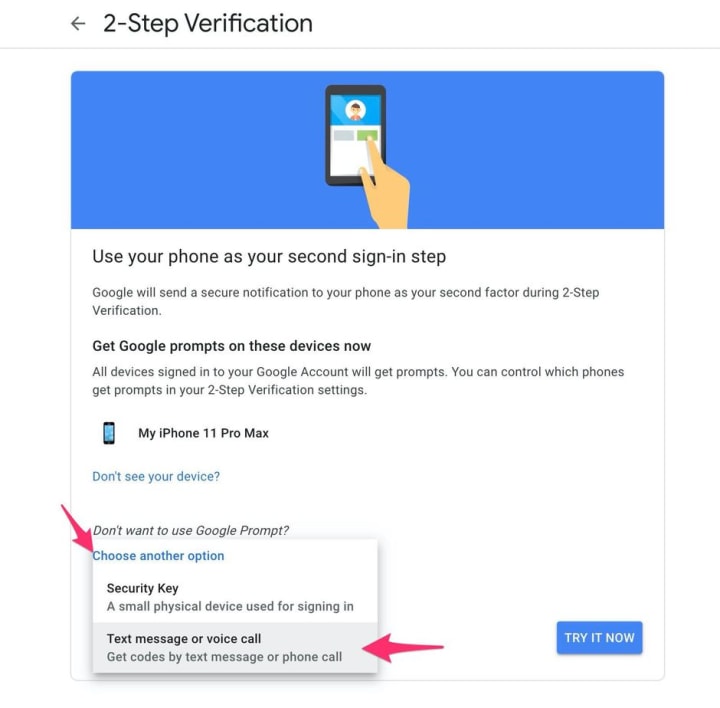
Using 2FA provides extra protection to an account. With 2FA enabled, Google apart from your password will also require an OTP either sent to you in a message or via the Google Authenticator. It is difficult to get the OTP without physical access to your personal device and after multiple login attempts, the account is blocked, until you prove you are the owner and unblock it.
Google offers a few options for this service; an authenticator app (like Google Authenticator or Authy or Salesforce) or an SMS code. If you use an Android device, you may also be able to set up an authentication notification on your phone, too.
But, wait, you're not done yet. Though 2SV via texted passcodes is more secure than not using 2SV at all, I recommend using push alerts if possible. SIM-swap fraud is becoming more common, allowing hackers to take over your phone number and receive 2SV codes meant for you.
If you must rely on passcodes, take a few extra minutes and set up an Authenticator app for your Google account. You can either use Google's Authenticator app or a password manager.
Click on Set Up under the Authenticator app section and then select the type of phone you use. Use your preferred app to scan the QR code, then enter the passcode generated by your app to verify everything is set up properly and you're done.
Remove access from non-essential apps--
If you have given account access to third-party apps and if they are compromised, your details can be leaked. So it is recommended that you keep on cleaning your account regularly and remove access from any non-essential apps.
Go to your account settings and then to the Apps section and revoke access from any third-party apps that you no longer use.
If it's an email app, it'll likely have access to your Gmail account and be able to send emails on your behalf. However, you may not have given it explicit permission to access all of your Google Drive content, for example.
Likewise, if you no longer use one of the apps in the list, you should remove it from your account. If you don't recognize an item on the list and don't believe you ever gave it access to your account, there is an option to flag it to Google by selecting the Report this app link.
Add account recovery options--
If a hacker is to gain access to your account or is able to block your account, you can enable it from the Settings option of Gmail.
With the help of recovery options, you can block unauthorized personnel from using your account without your permission. It will also intimate you if anyone were trying to access your account.
This is what Google will use should you get locked out of your account to verify you're the account owner.
Click on each section -- Recovery phone, Recovery email and Security question -- and update them with current information.
Again, if this information is out of date and you get locked out of your account, Google won't be able to verify you own the account.
Assess Recent Security Activity--
It's possible that a hacker (or an ex) is accessing your account without your knowledge. To check, sign in to your Gmail account and scroll to the bottom of the page. You'll see a line that says "Last account activity..."
At the end of that line, click Details to see when, how and where your account is being used. If you suspect any unkosher activity, click on the button labeled Sign out of all other Gmail web sessions and immediately change your password.
This area shows any login or access events in the past 28 days. Each item shows the device or app and date of the event. If you open a single event, there is more detail like the IP address, estimated location, and browser.
Although this is a read-only section, so you can't edit or change any settings here, it should alert you to whether any suspicious activity has occurred on your account. Google even has a prompt on this page, noting that if you see anything that looks suspicious, you should follow guidance to secure your account.
Ignore suspicious mails--
Many hackers trying to gain access to your accounts, send mails with phishing software attached to them, if you open such mails, you might end up in a big pool of trouble. So it is recommended that if you see any such type of mails, then steer away from them.





Comments
There are no comments for this story
Be the first to respond and start the conversation.