
After I published Part I of “How To Be Anonymous Online,” apart from people saying, “I have nothing to hide!” people strive to protect their data. If you follow all the steps in my guide, you had begun your journey to take back control of your privacy.
Recap from Part I:
- Change your Browser — Firefox and Brave are privacy-first web browsers. Or use Tor if you need extra features.
- Use Duckduckgo and the “private window” of browsers for searching.
- Check Your App Permissions and double-check the privacy settings on social media apps.
- Regarding Virtual Private Network (VPN) — Assume VPN providers keep logs and check if the provider support PFS — Perfect Forward Secrecy. Also, check the privacy law and regulations of VPN provider’s locations.
As mentioned, there is no way you can be completely anonymous while you are online. But the scale is not only one and zero. There is always more to be done when talking about privacy.
For Part II, I would go a bit deeper about privacy concepts, e.g., Zeo-Knowledge Proof and the steps that take us closer to anonymity.
The Most Expensive is “Free of Charge”

“Nothing can be more expensive than something for free.” (ただより高いものはない)
— Isaka Kotaro (伊坂 幸太郎)
Privacy is the ability to control who can access information about our private life and our activities, and it is critical because:
- Privacy is our right to choose our ideas and feelings, and most importantly, who to share with.
- Privacy preserves our private information, such as health or financial data, that we do not want to share.
- Without privacy, we are not truly free.
We would preferably pay for what we need, rather than the free things given. Before using a free app, you may ask yourself, “how is this company gonna pay their employees? ”, like Google and Facebook, do you know how they become the companies this big by offering “free” services to everyone?
In Japanese, there is an old saying that “nothing costs as much as what is given to us.” Why is it the most expensive? Because the price you pay does not measure with money but time, privacy, health, freedom, these intangible, which are our most precious assets.
Privacy Is Not "Individual-Only"
Online Privacy is not about locking the door when you go to the toilet. For each of us, as an individual, they are about autonomy, liberty, or protecting our digital self. For corporations and enterprises, the privacy of the employee is also vital for cybersecurity.
Hackers are not only skilled at computers. Some are also experts of “human hacking” —what we called social engineering attacks or blackmail. They target the key person within a company and study them. The more an attacker can learn about them, the more effective and effortless the attack would be.
Employee privacy, therefore, should be protected to mitigate the risk of social engineering and identity theft. Promoting the awareness of cyber hygiene is one way to do that. Instead, a few concepts should be bear in mind as an individual or an enterprise.
The D, A, P of Privacy

When we talk about online privacy, we seldom discuss the definition. Therefore, I would like to introduce the D, A, P in online privacy — De-identification, Anonymization, and Pseudonymitiztion, which are the idea of how we can process our data before sharing.
De-identification
According to NIST SP800–122 (Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)):
… de-identified information is used to describe records that have had enough PII removed or obscured…
Anonymized information is defined as previously identifiable information that has been de-identified and for which a code or other association for re-identification no longer exists.
De-identification is the process of working on removing personal information itself, while anonymization is the “product” of de-identification. While this may be unfamiliar to you, these methods are being used everywhere on the internet.
Between Anonymity and Privacy
Anonymity is often getting confused with privacy in the wrong context. Privacy relates to content — the data that can attribute a person, while Anonymity relates to an individual identity.
One way to de-identify your data is by encryption. An example is sending encrypted messages to a specific recipient. Only the recipient can read your message, thus protect your privacy. But encrypted data does not encrypt your contextual information, such as:
- Who are you talking to?
- When you send the message?
- How long is the message?
- How many messages?
All of the above cannot be encrypted; otherwise, the message cannot be read. As a result, they are easily discoverable by sophisticated attackers or governments with massive surveillance programs.
Anonymity
According to NIST-IR-8053 (De-Identification of Personal Information):
condition in identification whereby an entity can be recognized as distinct, without sufficient identity information to establish a link to a known identity.
When someone keeps their actions separate from their identity from a set of people, there is an equal probability of anyone in the group. Different from privacy, anonymity is when no one knows who you really are. At the same time, there is a possibility that the anonymous know what you are doing.
Pseudonymity
According to NIST SP 800–63–3 (Digital Identity Guidelines):
The use of a pseudonym to identify a subject.
Another way to hide your true identity is by faking it. A false online identity, or what we called “pseudonymity,” means using an alias or non-identifiable attribute to interact with others online. Using a nickname as your Twitter username, for example, can hide your identity, but people can still attribute activity to you.
Pseudonymity, in fact, is an excellent balance of privacy and accountability. But the decision is mostly dependent on the providers’ side, i.e., servers and applications instead of the client.
Zero-Knowledge Proof (ZKP)
Traditionally, there is no way you can allow access without any trust in it. The problem is where you store those attributes and data for users to access from nearly anywhere. When you check-in at the hotel, they will give you a key card to open a door lock. But the key card and safety are provided by them.
You need to put, if not all, at least part of the file sharing and application resources to the public so that dynamic authentication could take place. Zero-Knowledge Proof, in other words, is an encryption scheme trying to solve the problem.
The Principle of Zero-Knowledge Proof
Zero-Knowledge Proof is proposed initially in the 1980s by MIT researchers. It is a process by which certifying party can prove that something is right to the verifying party, with no additional information is disclosed except the specific statement.
For example, current websites store the hash value (hash value is the fixed-length output of a one-way mathematical algorithm) of the user’s password in their web servers.
For verification of the client, most websites use the process of hashing the client’s password input and matching it with the stored value, i.e., check if both hash values match.
Find Zero-Knowledge Services
Zero-Knowledge standards improve end-to-end encryption between you and the service providers as they ensure that the providers never have access to our files and encryption keys in a readable format. By that, when you check-in a hotel, you bring your own padlock to the assigned room that the hotel does not have access to.
It is the more reasonable way to protect your privacy online. Now you understand that whenever you pick an online service, it is better to find the one that comes with “Zero-Knowledge Proof You can search the service provider's official website to check if there is an agreement.
In short, do not blindly trust service providers.
ProtonMail — Encrypted Email Service
To prohibit the service providers from spying on you, like Gmail that actively scans your emails to deliver relevant ads to you, a fully encrypted email service is what you should have.
I used ProtonVPN, the company's VPN service when the “national security law ” was forced on Hong Kong last July—and now using ProtonMail as my prime email address ([email protected]).
According to the company website:
All user data is protected by the Swiss Federal Data Protection Act (DPA) and the Swiss Federal Data Protection Ordinance (DPO) which offers some of the strongest privacy protection in the world for both individuals and corporations.
As ProtonMail is outside of US and EU jurisdiction, only a court order from the Cantonal Court of Geneva or the Swiss Federal Supreme Court can compel us to release the extremely limited user information we have.
Scientists, engineers, and developers found ProtonMail to build an internet that respects privacy and is secure against cyberattacks. Several features are the reason that it gained a reputation in cybersecurity.
Encrypted Content Collaboration Platform
Just like ProtonMail can replace your Gmail, Tresorit is a Dropbox alternative with privacy protection in place. It s an end-to-end encrypted content collaboration platform. Protected by Swiss privacy laws, it offers enterprise-grade security to digital valuables using the cloud's highest classification.
Another Zero-Knowledge Service is SpiderOak, which provides a wide range of services for SMB to the enterprise. The company has been building products on the principle of Zero-Knowledge for over ten years.
Do What Snowden Said
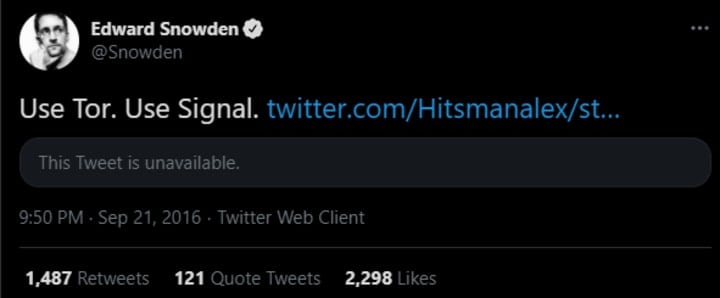
“Use Tor. Use Signal.” is a mantra from a Tweet by Edward Snowden. These two applications are a great start if you want to avoid surveillance.
Use Signal
Signal become famous after the recent “WhatsApp migration” after Facebook changed the user agreement of information usage. Please take a look at the Privacy Policy of Signal, and you would find that it is the shortest among all applications.

Signal Messenger is trusted by many technology leaders such as Elon Musk, Jack Dorsey (Twitter CEO), and Bruce Schneier (Security Expert). It is because:
- Open-source
- Peer reviewed
- Funded entirely by grants and donations, i.e., no drive to earn more
Use Tor
In Part I, I briefly introduced Tor Browser, an anonymization-based project called the short form of “The Onion Router,” an open-source software project for enabling anonymous communication.
While Tor browser route all web traffic via the Tor network to obtain anonymity in web browsing, you can also use Tor for all connections to be (almost) fully anonymous online.
Using Tor is not for general users as it required some knowledge of networking. But enabling Tor can maintain encrypted metadata for different protocols, which enhances anonymity overall.
Tor-based Router (Intermediate)
An option can help you protect multiple devices at once — using a Tor Router. One use case for me is traveling. Imagine you are going on a business trip to a censoring country, using a Tor router could help you to bypass the blocking and prevent spying at the same time.
Or, if you want to have a router at home that can provide Tor network connectivity at the network level, having a device like Invizbox or Anonabox could be a great start.
Tor-based OS (Advance)
There are plenty of operating systems aimed at achieving online anonymity. Below are several Linux distributions that can support privacy and anonymity.
Most of the time, this is for security professionals only, but if you are a privacy or technology evangelist, you can try them. The below can be run on a live system, i.e., to run the OS without installation but directly on a USB drive or DVD.
The Amnesic Incognito Live System — Tails OS
It is sponsored mainly by the Tor project, a Debian-based Linux distribution created to implement privacy and anonymity. All network traffic is routed within the Tor network, and all other connections are blocked (kill-switch).
SubGraph OS (Advance)
It is a Linux OS designed to resist malware. Critical applications run inside a sandbox to reduce the impact of successful exploits. This operating system has a hardened Linux Kernel and built-in Tor integration with a default policy that filters communication programs through Tor.
Final Words
For Part II, my goal is to give you more on thinking “why” and some advanced tools to go further than Part I (which is the kick-start for general users). The first thing to remember is the concept of “Free Service” which in most cases is the most expensive if you take into account intangible assets.
Also, privacy should be individual matters, as hackers would find and exploit employees' privacy data to launch social engineering attacks. Therefore, we need to learn more and enhance awareness in this matter.
I introduced the concept of “DAP” in privacy, which are:
Zero-Knowledge Proof (ZKP) is another keyword for you to choose online services that provide privacy-first technology or application. I gave several examples like:
- ProtonMail for encrypted email service
- Tresorit and SpiderOak for content collaboration
- Signal for messaging
Tor, in the end, is a purpose-built anonymity project.
- Tor Browser for private browsing
- Tor Router for traveling
- Tor OS for advance usage, Tails OS, and SubGraph OS
---
Thank you for reading. May InfoSec be with you🖖.
About the Creator
Z3n Ch4n
Interested in Infosec & Biohacking. Security Consultant. Love reading and running.
hackernoon.com/u/z3nch4n





Comments
There are no comments for this story
Be the first to respond and start the conversation.