
"All human beings have three lives: public, private, and secret." ― Gabriel García Márquez
A while back, I met an old friend who I hadn't seen since I graduated. We went for a cup of coffee to catch up for the past decades. He told me he was watching "Breaking Bad" in season 2. And we both love Breaking Bad (Who didn't?) I also recommended him to try Westworld as "Jessie Pinkman" was in last season.
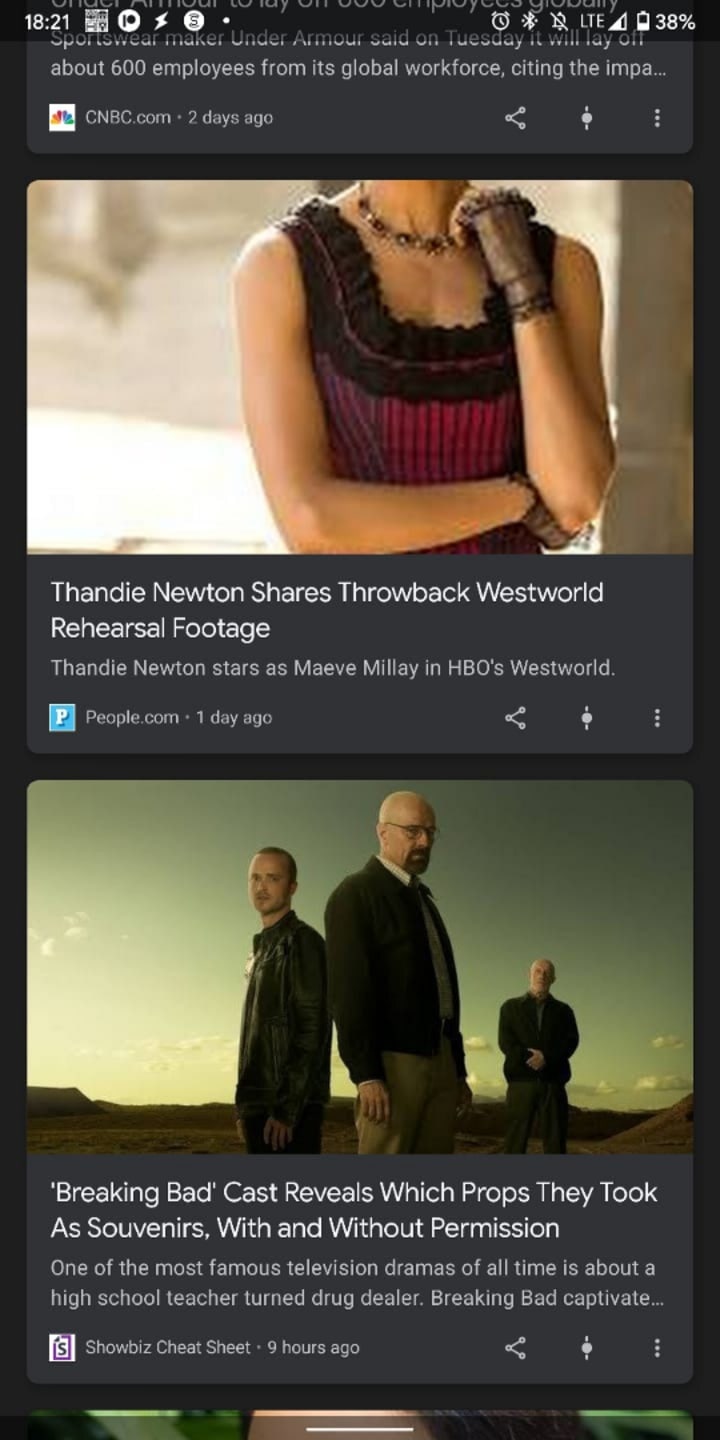
An hour later, what I saw on Google Now is gossip news about Westworld and Breaking Bad.
"Hey, Google. Stop spying on me!"
When I told him about my work and the recent privacy problems, he let out a chuckle. "I am not worried." He said, "Above all, I'm no criminal and do nothing wrong. I don't care if someone knows what I am doing online."
Listening to him saying, "I have nothing to hide!" saddened me. Not only am I a guy who has cyber cleanliness, but I have heard these arguments multiple times before. People think only criminals need to hide. Sadly, they do not know Privacy is our right.
Online Privacy, also known as Internet privacy or digital privacy, is part of cybersecurity for individuals. It is directly related to the confidentiality of the CIA triad. Confidentiality is, according to NIST:
Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
The Current Situation
Ideally, using the concept of Confidentiality in personal data implies two main ideas:
- Need-To-Know (NTK): Personal data is only disclosed when required.
- Least Privilege: The limit set to ensure the data access is aligned with the NTK of the subject.
But the reality is:
- Our data is collected and stored even when it is not required (Not NTK).
- Data are accessed by known or unknown adversaries (More Privilege).
- We even cannot locate where the data is stored.
Whether you do it consciously or unconsciously, we leave digital footprints. It is impossible to have ZERO footprints unless you are offline and live in a cave. We can at least reduce our footprint and manage our digital identity by implementing the concepts below.
Work From Home = New Threat Actor
In the light of the pandemic and the economic disruption that followed, data breaches increased over 2020. We may have taken some slack during the last year, but hackers did not.
According to the report of ZDNet, in 2020, there were several data breaches worth mentioning:
- IRS tax refunds: A US resident was jailed for using information leaked through data breaches to file fraudulent tax returns worth $12 million.
- Marriott: The hotel chain suffered a cyberattack in which email accounts were infiltrated. 5.2 million hotel guests were impacted.
- Nintendo: 160,000 users were affected by a mass account hijacking campaign.
I am sure you know all of them, or perhaps you even use them. They are not necessarily bad organizations. However, we cannot rely solely on them to protect our data. As data owners, we should pay more attention to what we share with them and how it is stored.
Big Brother is Watching You

The recent WhatsApp privacy policy change provoked a series of "digital migration" of internet identity. Although Facebook already delayed the new Terms of Service, I cannot see if someone is switching back to WhatsApp. My friend and I are now using Signal.
Google also collects tons of personal data, including all the searches and what YouTube videos we watched. They also track users' physical locations even the app is turned off.
It is now clear that we do not have our data ownership as we are supposed to. The Big Tech companies break their promises like what Facebook did to WhatsApp after the acquisition (The promise was "no ads, no games, and no gimmicks").
Digital Footprint 101
We need to know what it is before trying to protect it. Digital Footprint is everywhere on the web. It is all the actions from the keyboard and mouse, with the addition of what we tap and swipe on our beloved mobile phone.
Here are some typical locations that we leave most of our footprint.
- Social Media - not just what you post but the comments, like, tweet, retweet, and swipe left and right. Most platforms have very long user agreements that are difficult to read.
- Mobile Apps - Make sure you keep an eye on the updates of data policies and settings.
- Shopping Websites - the buying habits are precious for ads and marketing.
- Web Browsers - web browser uses headers and cookies as attributes that can let people identify who you are.
There's still hope - Digital Distancing
We now all know what social distancing is as it keeps popping up on the news. The idea of digital distancing is like when you want to talk to your boss about your salary rise, and you close the door. Keeping a digital distance could help keep you away from data breaches or eavesdropping for your digital self.
1# Change your Browser
It would be best if you had a web browser to surf online. But you may not know what data the site store and tracks. Tracking scripts and cookies are also alarming that developers may not be aware they captured more than needed.
Firefox is a popular choice and on the web for a while as it is fast and easy to use. It has built-in "trackers blocking" features and password vaults for users to protect their identity.
Brave Web Browser is a newcomer in the browser arena. It does not store any record of people's browsing history, making the browser the best privacy-preserving web browser.
One advantage of Brave is the support of the Chrome extensions. Therefore, you can switch from the memory-hungry application to this one and enjoy it. I use Firefox and Brave only, on mobile or windows platforms.
Tor is an anonymization-based project called the short form of "The Orion Routing," an open-source software project for enabling anonymous communication. And Tor Browser is an easy-to-use for anonymous web surfing.
Apart from what Firefox and Brave can provide, Tor Browser adds fingerprinting resistance and encryption to your browsing activities. Tor browser accesses the web via multiple hops to increase the difficulties of being traced back (directly increase the digital distancing).
It can also bypass censorship. People who use Dark Web would also take this extra precaution before accessing it.
Extra: Extensions and Settings Tips
I would suggest going the extra mile in the browser area. One addition is the ad-blocking extension. Brave has its built-in ad-blocking features called "Shield." I added the addon called "uBlock Origin," which both available on Firefox and Chrome.
Another bonus tip is, use a "private window" or "incognito mode" to surf if you do not need to log in or do not want to leave traces. One thing I would typically do is do Google Search using a private window. It can prevent Google from mapping my Google account with my searches. (You may easily change your internet search engine for DuckDuckGo in all your browsers.)
2# Check Your App Permissions
Regulating app permission is a significant part of privacy protection, and so permission should be granted based on the NTK basis. Recent news about malicious apps that abused app permissions to hijack our devices.
Not all apps are malicious but may mistakenly "over-request." Better to check the settings regularly, especially during updates and changes of user agreements.
Below is the list of data that your phone can leak to apps (iOS also has similar settings.):
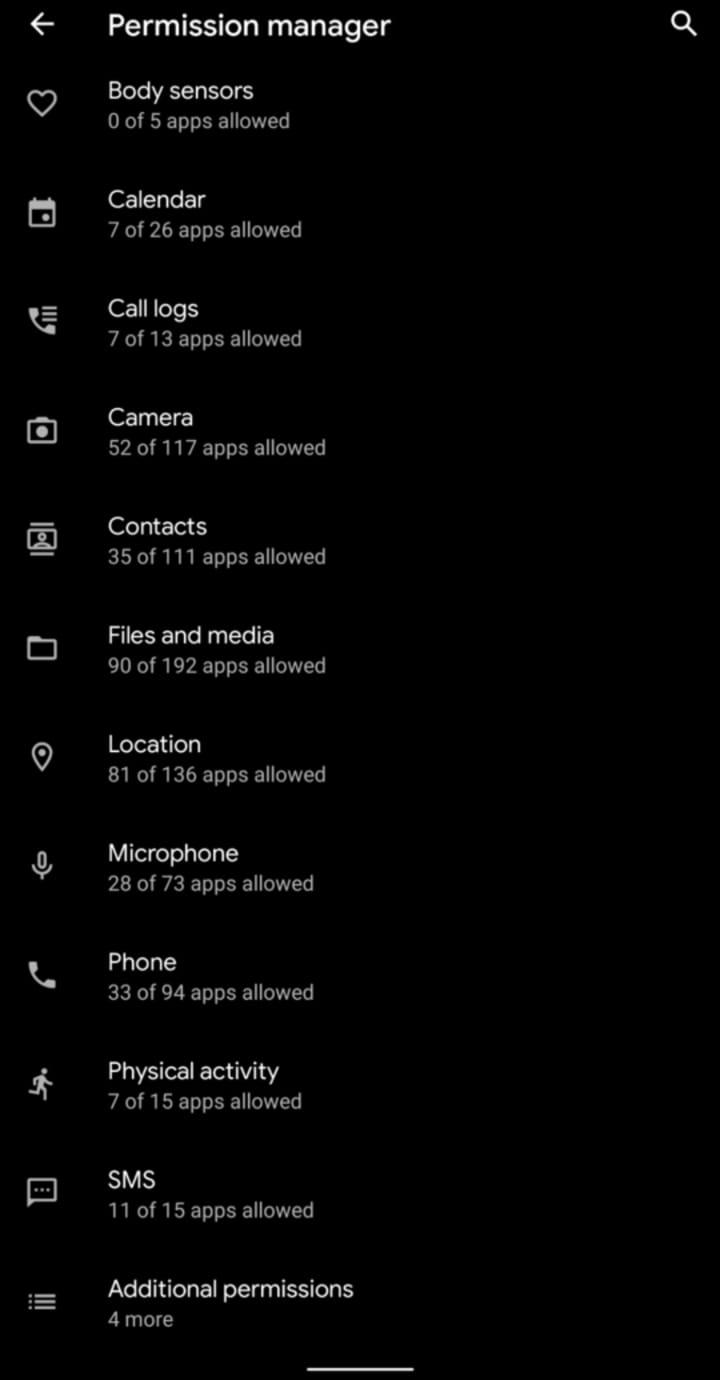
- Files and media - read and write files to the device.
- Calendar - allows the app to access or modify your events.
- Camera - allows the app to take photos or record videos.
- Contacts - allows the app to access your contact list and all your accounts used on the device.
- SMS - read and send SMS on behalf of you, combining with Contacts permission could make secondary impacts
- Location - GPS and cellular or WiFi data of your physical locations.
- Phone - access the phone info and call redirect. Also, it grants permission to the app to edit call logs.
- Microphone - can use to record audio without clicking a button.
- Body Sensors and Physical Activity - may contain some biomarkers like heart rate (from the paired device), step count, or sleep data.
Double-check!
I would suggest doing a double-check about the privacy settings on social media apps. Both iOS and Android have settings for a particular app. For example, if I want to review the Facebook app to see if it has the microphone permission:
- On Android - Long tap the app and click info, check if the microphone permission is granted.
- On iOS - open the Settings app, scroll down to Facebook, click on it, and check if the microphone is granted.
3# Upgrade Your DNS Security at Home
Protecting our DNS is an essential part of internet security. It is also a way to block many tracking scripts and apps to connect and send data back to their destinations. All internet-accessing devices would have a DNS setting. Better to protect your data from the beginning.

All you need to do is redirect the original DNS to a customized DNS provider on your devices. It also proffers you insights into the blocked DNS queries such as Blocked Reasons and Blocked Domains.
It also provides instructions on configuring the home router (intermediate skill required) for home settings. The prerequisite is that you backup the original settings before making any changes.
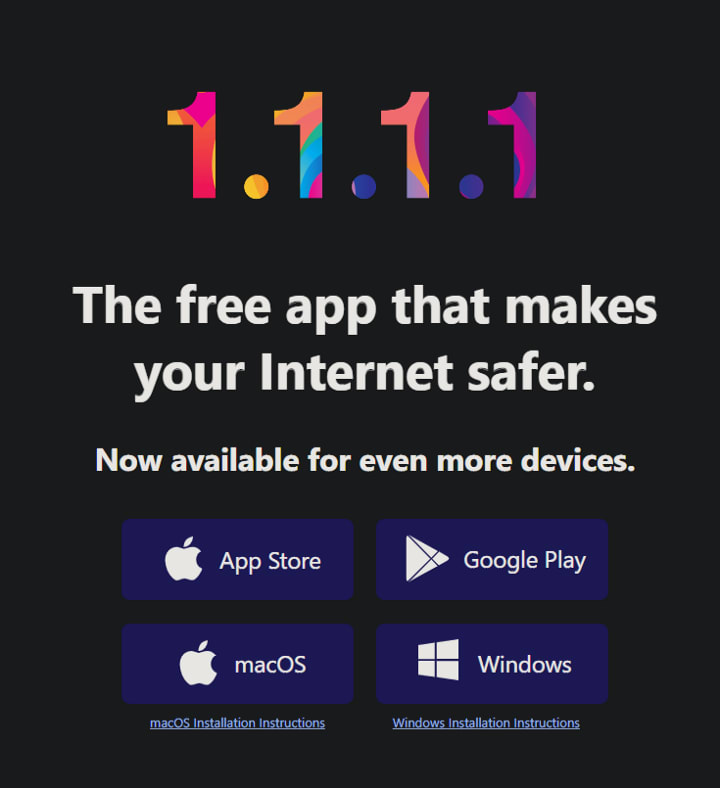
Cloudflare DNS
The DNS IPv4 address is "1.1.1.1". Cloudflare provides free DNS encryption since 2014. One bonus of Cloudflare is it can accelerate our browsing as the company is originally a content distribution provider.
The most straightforward setup is to change your original DNS to "1.1.1.1" and "1.0.0.1". The service also provides multi-platform support, and configuration is minimal. When you type "1.1.1.1" on your browser, you will get to the page that contains the installation instruction as below:
NextDNS
Another free-to-use DNS provider is Next DNS. It provides a wide range of protections, from malicious websites to ads and trackers. Like Cloudflare, it provides an agent-less, configuration-only setup and agent-based installation.
To start, go to the NextDNS website and click "Try it now." For long-term use, it is required to register an account. There is a Privacy tab for customization. The "Native Tracking Protection" option can block the native tracking of specific devices (Apple, Windows, Alexa, Roku, Samsung, Xiaomi, Huawei, and Sonos).

4# Virtual Private Network (VPN) - Good and Bad
(I simplified the VPN concept here, i.e., VPN can work in a non-tunnel mode.)
A tunnel from your laptop to the world-wild-web could prevent ISP or intermittent servers or companies from watching you. This is one example of being anonymized by using network encryption as a de-identification tool.
Creating a private network inside the public connection is like putting yourself in a tent in a Starbucks. No one can see through the tent, and so you can have your privacy. VPN is also useful when accessing the internet via a public connection, like an open WiFi that requires accepting agreements.
Not All VPNs Are Born Equals
In some sense, VPN is just a better version proxy in which the VPN provider can still see all your traffic, as they are the ones who help you encrypt and decrypt the tunnel.
There is no way to verify if the VPN provider does not keep logs. That is why we should pay attention to the selection of VPN providers. I found out this when China directly enforced the "National Security Law" on Hong Kong in July last year; as we have concerns about freedom and privacy, there was a rise in VPN subscriptions.
A string of "zero logging" VPN providers have some explaining to do after more than a terabyte of user logs were found…www.theregister.com.
The worst of all, there are 7 of them that claimed "zero-logging." To avoid the problem, better to assume VPN providers keep logs.
As a result, it is wise to pick the one with full control of its data center and storage. Using a VPN with a headquarter in a country with better regulations and privacy laws (such as GDPR for the EU) could provide greater assurance.
Another thing is to check if the provider support PFS - Perfect Forward Secrecy, a better protocol for encryption keys against future compromise even private key is lost.
Final Words

For our digital self, we should value our data as the real world. We have vaults to store our personalized jewelry, and we only share our financial records with the bank.
There is no 100% anonymity on the internet. Every time you tap on your phone, you leave some traces. But it is not about being invisible to others because it would be impossible to interact with others.
All the tools on hand do not immediately make you anonymous, but your awareness did. We need to, at least, try our best, take back control of our data. Privacy is fundamental to the internet and net neutrality. We should prepare ourselves for the next Big Tech company, saying that we want more and say no this time.
Below is the summary of how to take back control of personal data:
- Change your Browser - Firefox and Brave are privacy-first web browsers. Or use Tor if you need extra features.
- Check Your App Permissions and double-check the privacy settings on social media apps.
- Regarding Virtual Private Network (VPN) - Assume VPN providers keep logs and check if the provider support PFS - Perfect Forward Secrecy. Also, check the privacy law and regulations of VPN provider's locations.
Thank you for reading. May InfoSec be with you🖖.
About the Creator
Z3n Ch4n
Interested in Infosec & Biohacking. Security Consultant. Love reading and running.
hackernoon.com/u/z3nch4n






Comments
There are no comments for this story
Be the first to respond and start the conversation.