How Does the Dark Web Work?
It's totally anonymous, and has its own applications. So, how does the Dark Web Work?

The Dark Web is now a famous corner of the internet that worries police, parents, and corporations alike. Though it's gained notoriety as the birthplace of Bitcoin and the area of origin for a number of insane horror stories, not many people really know much about the Dark Web.
For most of us, the mechanics behind the Dark Web is sketchy at best. Even those who have visited the Dark Web ask, "How does the Dark Web work?"
If you're not in the know, you might as well get a crash course in the way that the Dark Web works. After all, it's pretty interesting stuff.
How does the Dark Web work differently from other parts of the net?
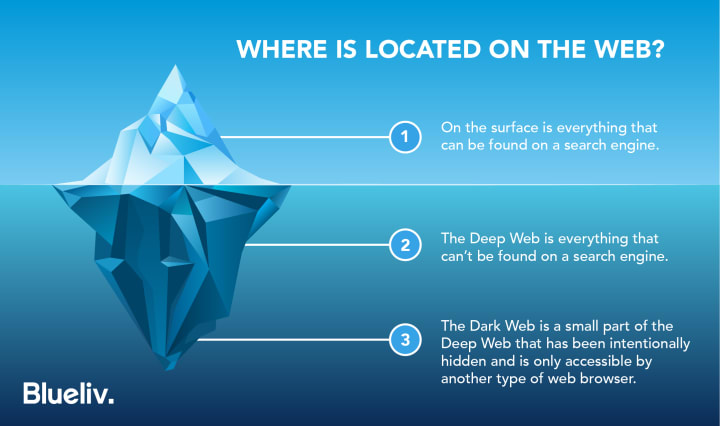
In order to understand how the Dark Web works, you need to understand a couple of things about its access points and how it's different from other networks.
First off, it's important to understand that the Dark Web isn't the same as the deep web. The deep web is just the portion of the web that Google and other search engines haven't categorized or made searchable.
The Dark Web is actually a very small, private section of the deep web. It's not only uncategorized by Google; it's also a private-access section of the net.
Here's how the Dark Web functions differently from deep web sites...
The Dark Web is a portion of the internet that can only be accessed using certain platforms or certain passwords. It's not meant to be public, per se. It's not cataloged like a regular site on a search engine; it's "dark."
The entirety of the Dark Web is literally an encrypted part of the internet — so that means there's no way to sidestep the need for specific software or passwords if you want to access it. If you want to unlock the encryption, you will need to use the right access tools.
Generally speaking, when people talk about private networks that aren't accessible via normal means, they call them darknets. However, for the sake of this article, the Dark Web will really only refer to the largest darknet of them all — the one accessed via Tor.
Tor is a set of internet security tools that were bundled up and added to a customized version of Mozilla Firefox. As of right now, it's the most popular software that features Onion encryption use, but there are many more alternatives you can check out, too.
The Onion Router uses Onion encryption to help people avoid being traced by their online activities. This is a hint as to why the URL of every Dark Web site you've probably heard of ends in ".onion."
How does the Dark Web work with Onion encryption?

As you might already know, most Dark Web sites that have made the news end in an onion address. The name "onion" here really does make a huge allusion to how the Dark Web works. Every packet of information is sent via layers of encryption and protective coding — much like how onions have protective layers, too.
Tor works by encrypting all the user's identification and then passing the user's IP address through Tor nodes. This sends all the information through randomized relays that only reveal small portions of information at every time. As a result, tracing it is fairly difficult.
This is called Onion encryption, and every layer makes it harder to track down something identifying about the person's identity. For the most part, Onion encryption is considered to be untraceable.
However, it is possible to de-anonymize users by finding weaknesses in the broswer that Tor is attached to. Tracking down website owners and site users has happened in the past — and as darknet stuff continues to grow in popularity, it will continue to happen.
This is very fascinating, considering how often raids due to the Dark Web get featured on the news.
How does the Dark Web work to keep things untraceable with all the law enforcement scrutiny it receives?
The funny thing about the Dark Web most people don't realize is that it's actually funded by the United States government. Up until the late 2000s, it was a military network.
The reason why it's so hard to trace is because it was designed by top military scientists to be an untraceable way to send information via the internet. Unfortunately for law enforcement, it was way too well-designed to trace criminals, too.
Oddly enough, neither Tor nor any "darknet" servers really work with law enforcement, per se.
However, US government officials and law enforcement groups have set up "honeypot" sites that catch criminal interactions in hopes of actually being able to unmask who's behind the computer screen, such as those behind Silk Road. This is how pedophile rings and red room owners have been caught in the past.
Additionally, other online groups are working to try to help remove the masks behind the criminals as well — many of those groups being online vigilantes.
So, how does the Dark Web work for its users?

This can be a tough question to ask. Overall, it seems to work well for its users — just not how you'd expect it to work.
Believe it or not, the vast majority of people who use Tor aren't actually cyber criminals or intrepid explorers. Of the 2 million people who use Tor, the vast majority of them use it for daily browsing on mainstream sites. Why? Because they like privacy.
That being said, the Dark Web is way smaller than you think. Unlike the deep web, which is just uncatalogued websites, the Dark Web is actually just a small corner of "off-web" websites. Experts estimate it to be only 30,000 sites in total.
So, it works as a private web browsing software, with an added perk of extra sites. How you use it is totally up to you.
About the Creator
Riley Raul Reese
Riley Reese is comic book fanatic who loves anything that has to do with science-fiction, anime, action movies, and Monster Energy drink.





Comments
There are no comments for this story
Be the first to respond and start the conversation.