Cryptography in Information Security: A Brief Analysis
When the concept of a computer saw its first inception by the genius engineer Alan Turing during World War II, it was designed for the sole purpose of cracking the German Enigma machine; in other words, computers and our advanced modern technologies were born out of the phenomena known as cryptography.

It soon became apparent that the necessity of automated tools for the sake of file protection and additional information stored on computers must become mandatory. However, the science of cryptography has existed well throughout the majority of the course of human history; dating back as far as 1900 BC during the age of the Egyptians and their Old Kingdom.
Existing as both a science and an artistic medium of expressing communications, cryptography “applies complex mathematics and logic to design strong encryption (disguised plaintext) methods”. In the modern digital age, it is the essential tool that allows businesses, governments, and individuals to maintain the privacy of network users and protect classified information without much concern for deception or theft.
The original design philosophy and goal behind the utilization of cryptosystems (confidentiality) metamorphosed into applications that existed to preserve the integrity of information. This started precisely during the dawn of the Information Age in the 1990s when generations of individuals began conducting their businesses online and started to transfer hundreds of millions of dollars electronically.
Now into the modern-day, this trend has spread throughout the vast majority of the human civilization; where thousands of people interact with electronic devices on a daily basis through the utilization of ATM machines, cell phones, e-commerce, and emails.
At the same time, the rise of black hat hackers who interact with systems using nonconventional methods with intentions to steal private information skyrocketed. As such, the exponential growth of digitally transferred data resulted in an explosive reliance on cryptography for the sake of authentication and information security.
Perhaps the most basic way to explain the concept of cryptography lies within the existence of one of the earliest known cryptosystems known as the Caesar Cipher. Better known for the more understandable term Shift Cipher, the concept is taught within universities utilizing three hypothetical characters: Alice, Bob, and Eve.
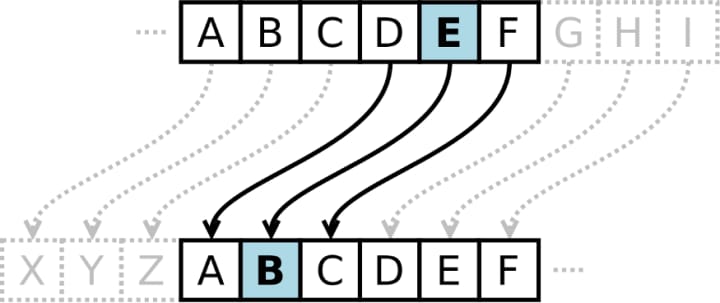
If Alice desires to send a message (plaintext) to Bob without allowing anyone else to understand what she is saying, she can utilize a Shift Cipher to disguise her plaintext. Within the plaintext lies the word: “Hello”.
She encrypts the message for every letter of the English alphabet that exists within her plaintext: “H” “E” “L” “L” “O” through “shifting” every letter backward in their alphabetic position three times. This method of Shift Cipher encryption (one of thousands) is precisely what creates the cipher itself; also known as the key.
As Bob is the only person possessing knowledge of the key, he will take the now encrypted message (known as the ciphertext: “EBIIM “, and subsequently decrypt it (unlock the plaintext) using the key for Alice’s Shift Cipher. Once completed, he will successfully interpret the original message as “hello”.
Despite the fact that this cipher is a very poor and easily crackable cryptosystem, it was quite successful in its implementation for many decades. Due to the fact that the knowledge of cryptography has permeated throughout research institutions for thousands of years, modern cryptosystems have evolved to become astronomically more complex; a feat accomplished only through the power of computation and information technology (IT).
Although humanity’s exponential progression in the growing field of technology has allowed us to create encryptions that would make even the world’s most powerful supercomputer millions of years to decrypt (computationally secure — the main pro of using technology to solve security issues), it has still failed in its attempt to establish a perfectly secure system (no matter how many attempts, nothing is learned from the pattern of the ciphertext — the main con of using technology to solve security issues).
Today, these computationally secure systems are broad in scope; inheriting many thousands of manipulations in multiplicative calculus to encrypt billions of dollars worth of information. One of the most famous and well-known of these modern cryptosystems that even my own organization uses to protect bank accounts (including my own) includes the utilization of public-key cryptography.
While also commonly referred to as asymmetric cryptography, this particular system is an encryption scheme that takes two keys in relation to one another via mathematics yet is different in identity to protect plaintext. The two keys are known as public and private, respectively. Despite the fact that algorithms using symmetric cryptography possess a similar pattern such that they solely rely on the use of one key for the sake of encryption and decryption, both of those utilized in public-key cryptography inherit unique functionalities. What makes this particular cryptosystem so powerful and so secure is the fact that “it is computationally infeasible to compute the private key based on the public key”.
As such, these public keys can be shared freely to anyone using the network; allowing the user base a convenient and simple method for the sake of encrypting content and verifying what is known as digital signatures. These digital signatures are any content that is signed digitally through the use of a person’s private key and is processed for verification via their public key. Moreover, the uselessness of the public key for decryption purposes allows the private key to exist as an easily kept secret, ensuring that only the private key owners can discover necessary information.
Due to the fact that these public keys are to be shared with many different people yet are far too large for the average person to memorize, they are instead stored on what is known as digital certificates that allow secure sharing and transportation. As the private key is a closely guarded secret that is not to be shared with outsiders, these are stored within either the operating system, software, or simply hardware that the network/computer utilizes that contains the necessary drivers to interact with the software.
The aforementioned digital certificates become issued via entities called Certificate Authorities, or simply CAs. Given the rapid pace of growing concerns for clientele; especially in the field of online commerce and the impact legislation has on information security, more and more companies are becoming compelled to allocate additional resources in computationally secure cryptosystems. Unfortunately, expenditures related to these concerns are met with increasing amounts of scrutiny at the same time.
Administrators of IT departments that handle information security for businesses are now under constant pressure to maintain the argument to senior management officials for necessity relating to these cryptosystems.
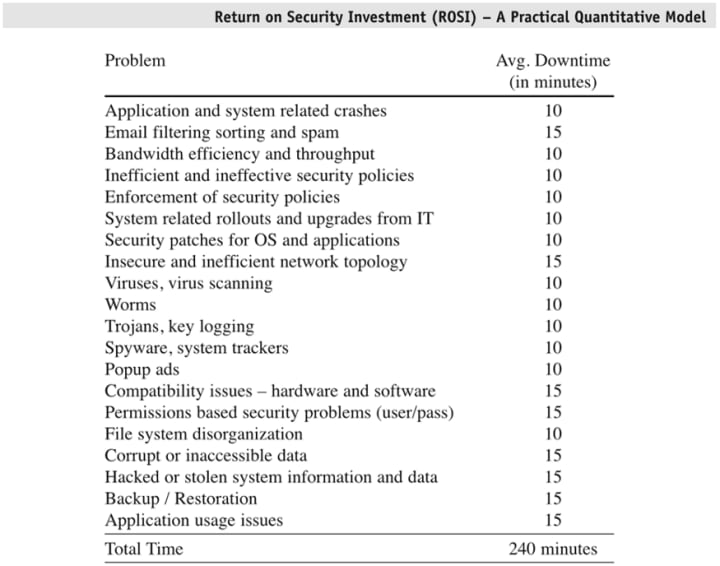
To assist in this goal, a survey conducted in joint partnership with the FBI and the CSI has started to embrace economic metrics and systems therein to provide a steady flow of validation to these kinds of services. For example, return on security investment (ROSI) explicitly states that both financial and non financially related benefits of information security compared to the increasingly expensive costs.
The driving forces behind the utilization of ROSI include the assistance of project selection and appraisal / the provision of general input for the sake of management with regard to information security. This method is primarily driven by management officials, economists, academics, and security professionals. Unfortunately, ROSI comes with the inherent downside of potentially being subjective with regards to estimating risk and damage mitigation.
Attributes of time present the main problem associated with the subjectivity, and as such, a lot of managers have turned to the coprocessor known as Net Present Value (NPV) for the justification of cryptosystem expenditures. During the process of evaluating alternatives, NPV works efficiently such that its modus operandi is to locate the flows of cash generated by a given solution and uncover the value of the flows using the current inflation rate of the dollar.
Today, NPV has evolved to become the most popular accepted criteria to evaluate projects in corporate finance. Any project that demonstrates a positive NPV will inherently increase the given firm’s overall net worth. In other words, “the total value generated through the project’s lifetime is superior to the cost of financing it”. Finally, the last well-known economic mechanism for driving the utilization of information security systems includes what is known as the Internal Rate of Return (IRR).
Generally speaking, IRR stands as the final metric of economies in the pool of discussion for a manager to consider using when evaluating the potential cryptosystem expenditures associated with a given project. Utilizing the exact same formula for cash flow as its NPV counterpart, IRR simply allows a manager to view the rate at which a given organization will break even on their investment to the cryptosystems.
Overall, the true costs behind the utilization of much-needed security measures and possible breaches are multi-faceted in their anatomy and as such are extremely difficult to properly quantify. Any impact on business with regards to a possible breach of information can be classified into the four categories of impact including financial, operational, customer-related, and employee-related. Still, the necessity of information security in everyday IT networks and systems is too critical to do without.
About the Creator
Arbiter Writing
A freelance content agency with over 6 years of experience in the field of professional writing and editing services. We perform research based on topics of clients' choosing and provide SEO-optimized blog posts, articles, and copywriting.





Comments
There are no comments for this story
Be the first to respond and start the conversation.